
Due to the sensitive nature of the work performed, a Non-Disclosure Agreement (NDA) was signed with the client, preventing the disclosure of their name, location, and specific infrastructure details. This case study highlights the key cybersecurity challenges faced and the solutions implemented while maintaining client confidentiality.
Cyber attacks can happen to any company in this digital world; it’s just a matter of when. The team at P.I.V.O.T Security are experts in handling critical situations like these and provide dedicated expertise for incident responses for all organizations. We believe in crafting custom processes and plans based on the requirements and structure of the organization we are working with.
In this case study, we will talk about one of our healthcare clients whose database was compromised by a sophisticated threat actor. The client requested us to perform an IR (Incident Response), identifying the root cause, conducting assessments of the data loss (if any), and eradicating the threat.
The client’s server was compromised by an adversary. The attacker gained access to their database, exposing sensitive Protected Health Information (PHI) and Personally Identifiable Information (PII) of more than 10,000 customers. This posed a significant risk to the organization’s operations and compliance, especially with regulations around healthcare data protection.
We understood the web application was compromised. Once P.I.V.O.T was onboarded, our task was to understand the actual root cause and patch the web application.
Client Tech Stack:
Our team was brought in to handle the situation through a complete Incident Response (IR) plan. During the onboarding, we signed an NDA before starting the process. First things first, the P.I.V.O.T team assigned dedicated roles and responsibilities among their team members and with the client. This helped in formulating a core team for the IR process to accomplish the goals.
We submitted a basic report with the insights we gathered. We began with an IR, then performed a full audit of the web applications and the organization’s entire asset inventory to find weaknesses, and finally helped apply patches to secure their systems.
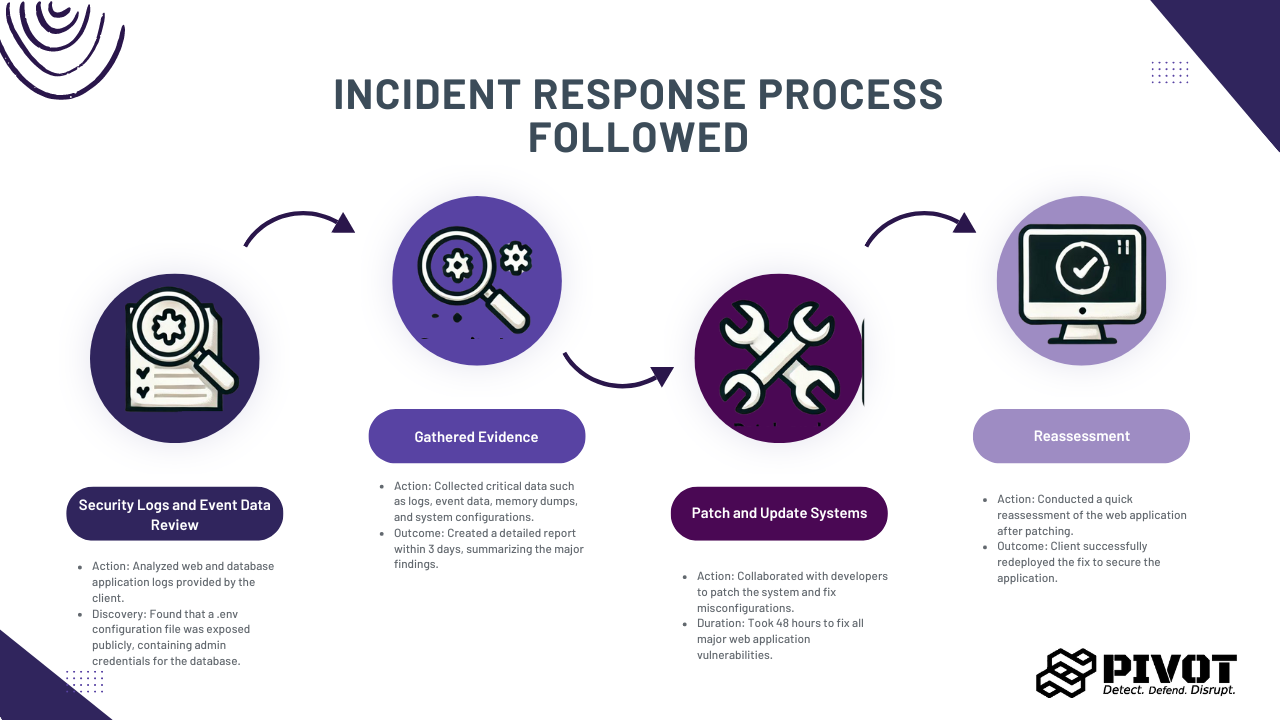
Security Logs and Event Data Review:
The client provided us with the logs of their web and database applications. We analyzed them, and within two days, we figured out that a .env config file of a web application was exposed publicly. It contained admin credentials for the database.
Gathered Evidence: Our team collected logs, event data, memory dumps, and system configurations for proof. On the 3rd day, we quickly created a report explaining the major findings.
Patch and Update Systems: Once the finding was clear, the process of patching started. Our team sat with the developers and helped them patch the system and fix the misconfigurations. It took almost 48 hours to fix all the major web applications.
Reassessment: We did a quick reassessment of the web application that was exposed, and the client redeployed the fix.
Web Application and Asset Audit: We performed an in-depth audit of all web applications and assets. Tools like BurpSuite Professional and HCL AppScan were used to scan for vulnerabilities across their web applications. For some applications, we manually detected vulnerabilities along with the app scans.
Database and Asset Review: Since the database was breached, we reverified the security configuration, admin details, authentication, and authorization of all the storage and data processing systems to ensure the safety of the PHI and PII data post the incident response.
Compliance Standards Maintenance and Review: Once the above activity was complete, within two weeks, our team was tasked with reviewing the security policies according to various information security and data privacy standards, including ISO-27001, HIPAA, and GDPR. We ensured the major policy rules were followed.
Our team’s effort led to a complete root cause analysis of the issue, ensuring that the threat actor didn’t have access to the database anymore and PHI/PII data was secured. The data of more than 10,000 customers was lost initially, but we made sure it was secure post-incident. The organization experienced minimal operational disruption and was able to maintain business continuity.




