Mitigating a Ransomware Attack for a Healthcare Organization
Non-Disclosure Agreement
Due to the sensitive nature of the work performed a Non-Disclosure Agreement (NDA) was signed with the client preventing the disclosure of their name, location, and specific infrastructure details. The case study highlights the key cybersecurity challenges faced and the solutions implemented while maintaining client confidentiality.
Executive Summary
Cyber attacks can happen on any company in this digital world—it’s just a matter of when. The team at P.I.V.O.T Security are experts in handling critical situations like these and provide dedicated expertise for incident responses for all organizations.
At P.I.V.O.T we have always believed in the customization of services and solutions for our clients. This is a case of a leading healthcare organization (revenue of 1000+ crores) with a hybrid infrastructure comprising both on-premise and cloud-based systems that faced a significant cybersecurity threat. Given the sensitive nature of the client's operations and the presence of sensitive data (PHI and PII), immediate and effective incident response (IR) was critical to minimize business disruption.
Key Highlights
Key Challenges
- Production servers were infected with ransomware called CryptoMine
- 1800+ systems were impacted
- PHI and PII data involved
- Core business funcitons impacted
Solution
- Immediate containment and eradication of ransomware
- Active Directory system recovery
- Critical patching and vulnerability remediation
- Physical forensic through client's laptop
Resources and Timelines
- Less than 24 hours of downtime for business
- Completed the IR process with reports in 15 days
- Only 2 resources required from client side, one managerial and one technical
- Source code reviews and audits
- Continous SOC monitoring with dedicated security analysts of our team
- Continuous security posture assessment
- Phishing simulations and security awareness trainings for employees
Problem Statement
The healthcare organization was hit by a ransomware attack—specifically the CryptoMine ransomware strain—affecting 1800–2000 systems. The servers were used for mining, leading to server exhaustion. The client became aware of the server exhaustion through their logs of EDR systems but was unsure of the infection and data loss, if any. The attack compromised their Active Directory (AD) controls, leading to potential exposure of personally identifiable information (PII) and protected health information (PHI).
Tech stack of the client:
- Hybrid cloud infrastructure with multiple vendors
- Public and on-prem infrastructures
- Oracle Database
- Apache Tomcat Server
- Javascript frameworks used for applications
Solution
The above challenges were not easy to overcome and required a comprehensive Incident Response (IR) plan to address the attack. The time was of critical essence, and with business operations paused, it became more critical for us to work on tight deadlines. To cater to this we followed a structured approach involving root cause analysis, identifying the entry point of the ransomware, ransomware analysis, separating production servers, system restoration, and the implementation of preventive security measures.
IR Process followed
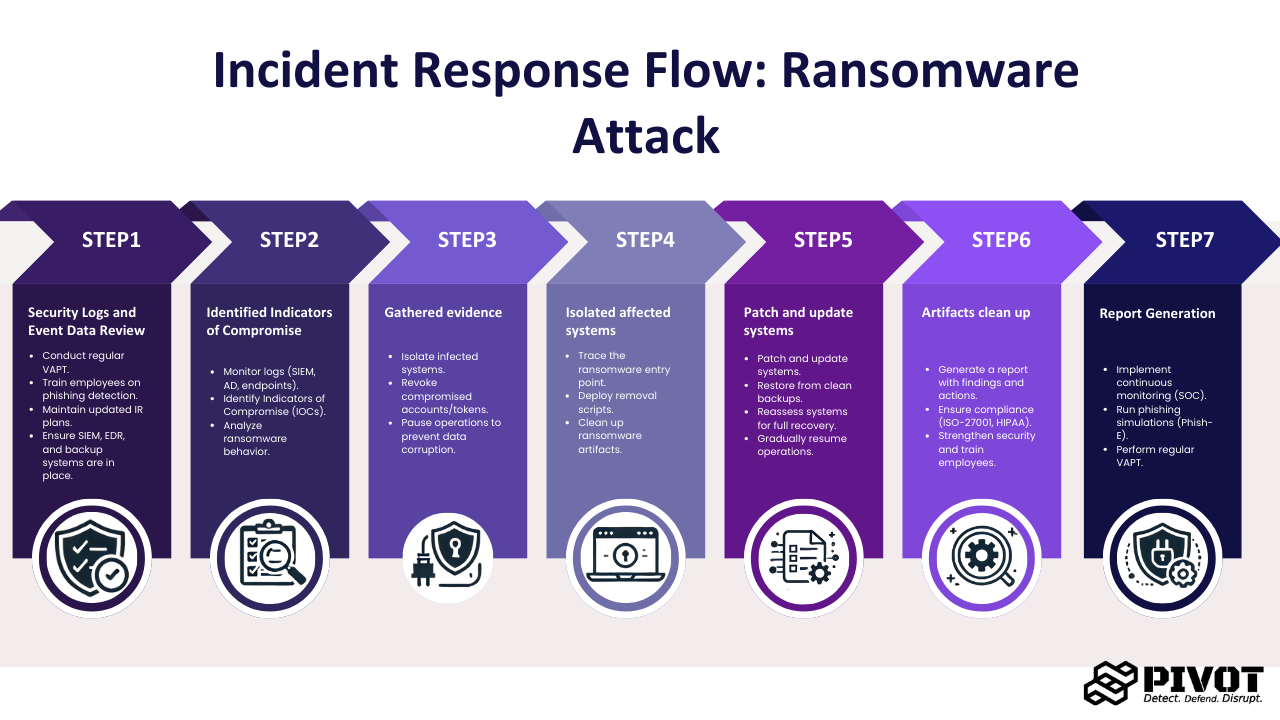
- Security Logs and Event Data Review: Analysed domain controller logs, Security Information and Event Management (SIEM) alerts, and endpoint logs for unusual patterns (e.g., mass account lockouts, privilege escalations, suspicious logins).
- Identified Indicators of Compromise: Checked for anomalous activity such as abnormal Group Policy Object (GPO) changes or privilege escalation. Confirmed the IOC in 24 hours.
- Gathered evidence: Our team collected logs, event data, memory dumps, and system configurations for forensic analysis. Within 2 days we confirmed the entry point through logs. The AD domain controller was compromised due to weak passwords and effective social engineering techniques.
- Isolated affected systems: After identifying the entry point on the 3rd day, we isolated the user, disabled the machine from the network, and revoked complete access. We performed a similar process with other impacted systems as well. The access tokens were revoked for the compromised accounts.
- Patch and update systems: Once the containment was successful, the process of eradication started. On the 4th day, we wrote the RTR script for the CryptoMine ransomware and deployed it on the AD domain controller. The password reset process was followed for all the affected accounts, starting with the admins.
- Artifacts clean-up: We started cleaning up the systems, making sure no artifact was left in the systems, including the ransomware, malicious scripts, scheduled tasks, or even shadow admin accounts.
- Report Generation: We started building a detailed report post the IR for the executives and team. It consisted of basic highlights and detailed remediation procedures taken care of by our team.
- Continuous security posture assessment: We implemented a rigorous security audit process for regular vulnerability assessments and penetration testing (VAPT). This allowed us to identify potential security risks in real-time and apply necessary patches proactively.
- Phishing simulations and employee training: Through our in-house phishing simulation tool Phish-E, we conducted organization-wide phishing campaigns to test and improve employee awareness. As a result, the organization witnessed a significant reduction in phishing attack success rates.
- Continuous SOC monitoring: A dedicated Security Operations Center (SOC) was deployed for 24/7 monitoring from our team at P.I.V.O.T Security. This included continuous tracking of system logs and mapping out any remaining or new threats to the infrastructure.
- Physical forensics: As part of our investigation, we requested a sample infected laptop from the client for in-depth forensic analysis. This allowed us to reverse engineer the ransomware and determine its full impact on the infrastructure.
- Source code reviews and audits: Comprehensive source code reviews were performed to identify coding errors and vulnerabilities that could be exploited by ransomware. These reviews contributed to the hardening of critical applications.
Compliance and Audits
Post-incident, happy with the results our team delivered for the clients, the client provided us with the contract to ensure full compliance with ISO-27001 standards. This involved conducting internal security audits and implementing necessary changes to meet healthcare regulatory requirements.
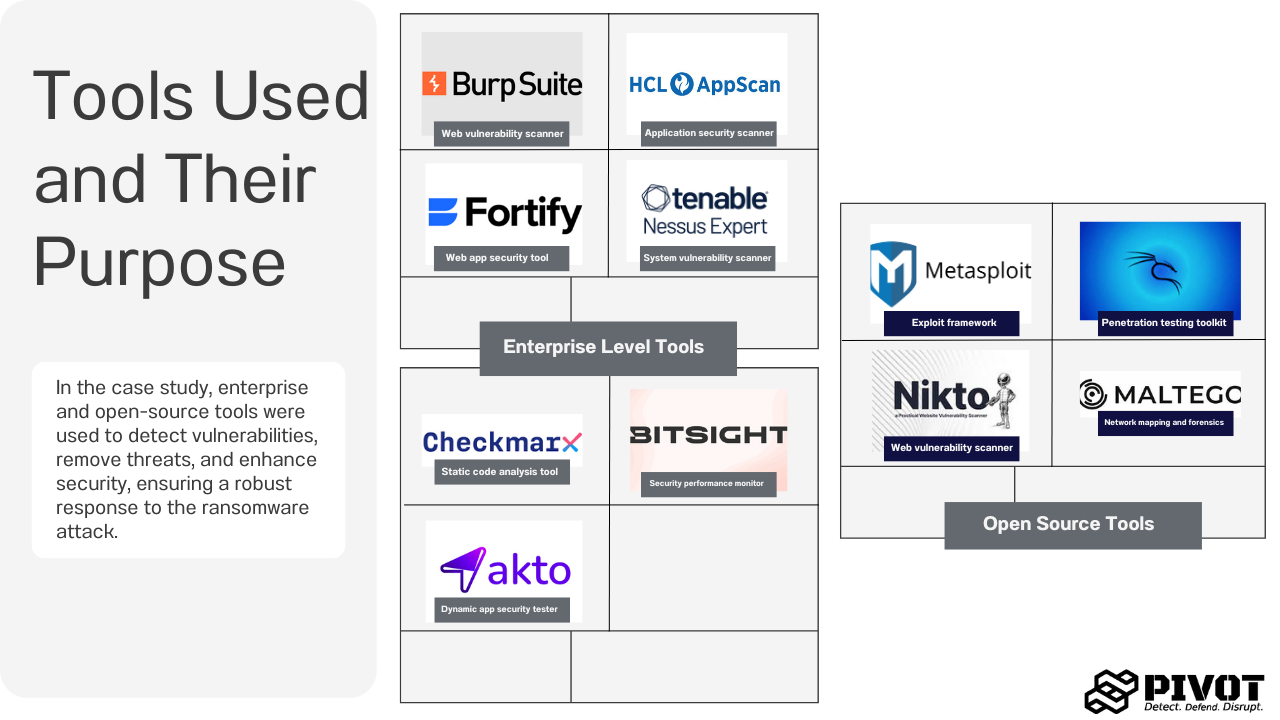
- BurpSuite Professional: A web vulnerability scanner used to identify and mitigate security flaws in the client’s web applications.
- HCL AppScan: Utilized to assess application security and ensure that the critical systems were free of vulnerabilities post-incident.
- Tenable Nessus Pro: A vulnerability scanner that played a critical role in identifying security gaps in the infrastructure.
- Fortify Web Scan: Focused on scanning web applications for potential threats and preventing vulnerabilities from being exploited.
- CheckMarX: Used for source code scanning, identifying security loopholes in the application code that could be leveraged by attackers.
- BitSight Pro: Monitored the client’s security posture by providing risk assessments and insights into third-party security performance.
- OpenText Fortify DAST: A tool for dynamic application security testing, helping to simulate real-world attack scenarios.
- Complete Kali Stack: A comprehensive suite of penetration testing tools that allowed us to simulate attacks and identify weak points in the network.
- MetaSploit Professional: Employed for exploiting vulnerabilities and validating security controls in a controlled environment.
- Nikto: A web server scanner used to detect outdated software and misconfigurations that could expose the organization to risk.
- Maltigo Hydra: Used for mapping the network, identifying relationships between systems, and performing forensic investigations on compromised devices.
Conclusion
Co-ordinated communication is a must for incident response (IR), and through our structured approach, we successfully remediated a major ransomware attack, restored the organization's security posture, and ensured that sensitive PHI data remained protected. The complete IR was done within the 15-day timeline with less than 24 hours of business downtime. Furthermore, our efforts helped the healthcare organization strengthen its compliance with ISO 27001 standards, positioning them for a more secure future.







