
Phishing is a deceptive technique used by cybercriminals to trick individuals into revealing sensitive information by impersonating legitimate entities. Government agencies are prime targets for phishing attacks due to the sensitive and valuable information they handle. Adversaries, including nation-state actors, seek to exploit these organizations to gather intelligence, disrupt operations, and undermine national security.
Over the past five years, several high-profile phishing attacks have targeted Indian government entities. For example, in 2019, the Indian Space Research Organisation (ISRO) faced a phishing attack where attackers impersonated officials to steal sensitive data. In 2020, a phishing campaign targeting the Ministry of External Affairs attempted to compromise official communications. These incidents illustrate the persistent and evolving threat landscape facing Indian government agencies today.
The recent breach of India's National Investigation Agency (NIA) serves as a stark reminder of the effectiveness of phishing attacks. In this case, the advanced persistent threat (APT) group SideCopy, originating from Pakistan, executed a sophisticated phishing campaign that compromised the credentials of government employees. This blog explores who SideCopy is, details the phishing attack, and demonstrates how Phish-E can simulate such threats to enhance cybersecurity awareness and preparedness of the organizations.
SideCopy is a notorious Pakistani APT group known for its espionage activities targeting South Asian entities, particularly Indian government organizations. Active since 2019, SideCopy mimics the infection chains of another APT group to deliver its malware payloads. Their preferred method of attack involves using phishing emails to deploy remote access trojans (RATs) like Action RAT, allowing unauthorized access to targeted systems and exfiltration of sensitive data.
To demonstrate the attack executed by Pakistani APT, we simulated the SideCopy phishing attack on NIA through our tool Phish-E. This simulation helps organizations understand how phishing attacks are executed, the tactics used, and potential threat vectors and train employees to recognize and respond to phishing attempts effectively.
Here’s a video simulating the steps in Phish-E.
In Phish-E, begin by navigating to the campaign management section through the side navigation bar. Here, you can initiate a new phishing simulation campaign for your organization. Phish-E stores the history of all the campaigns run previously and you can reuse or relaunch them in the future.
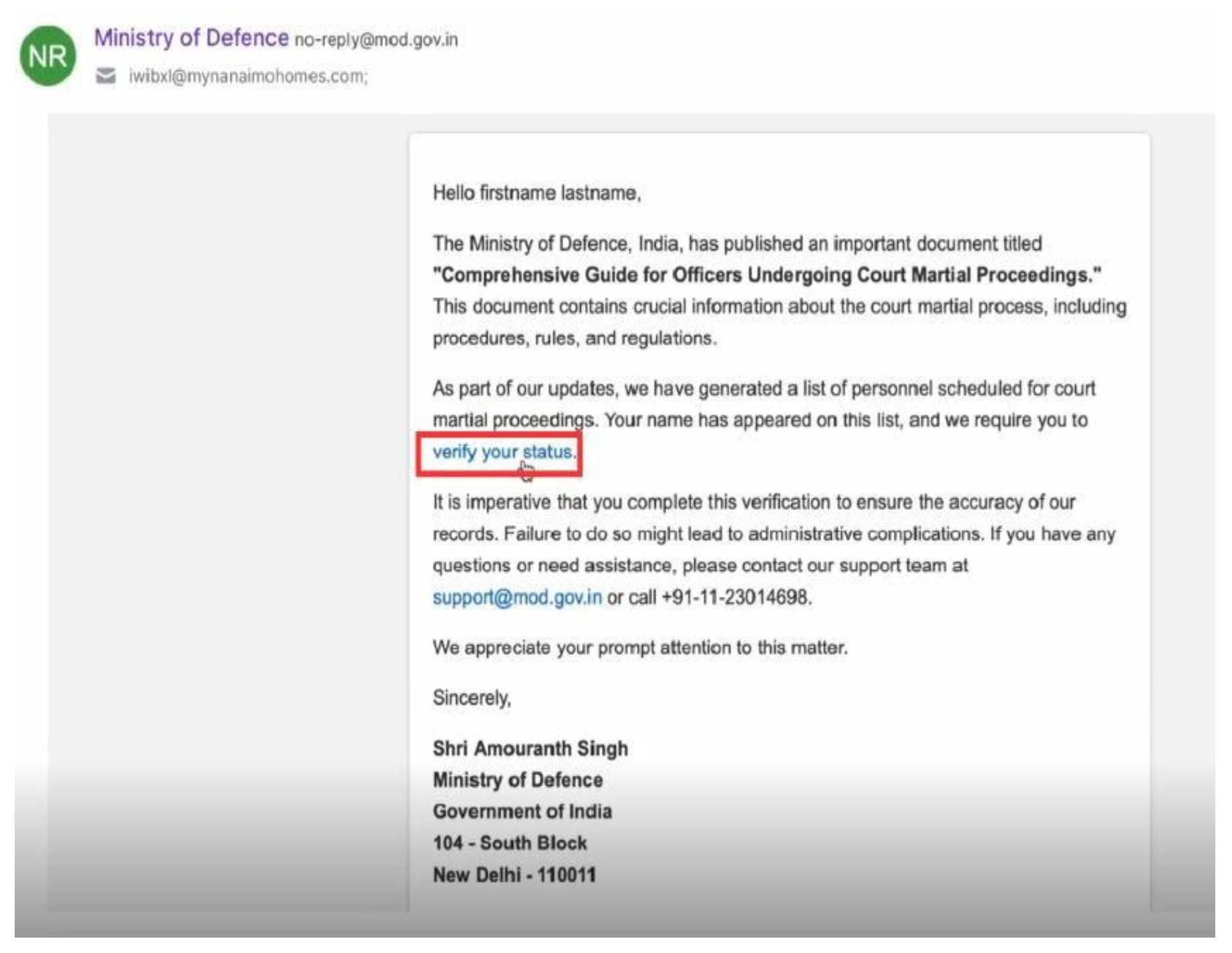 SideCopy carefully crafted the email template to trigger various emotions in the target user as shown above.
SideCopy carefully crafted the email template to trigger various emotions in the target user as shown above.
Phish-E provides industry-specific templates that reflect the latest threat vectors. These templates are designed for all organizations including government, public and privately owned companies. These templates are continuously updated to mirror real-world phishing attacks, ensuring that simulations are both relevant and effective.
Customizing the selected template by entering details such as:
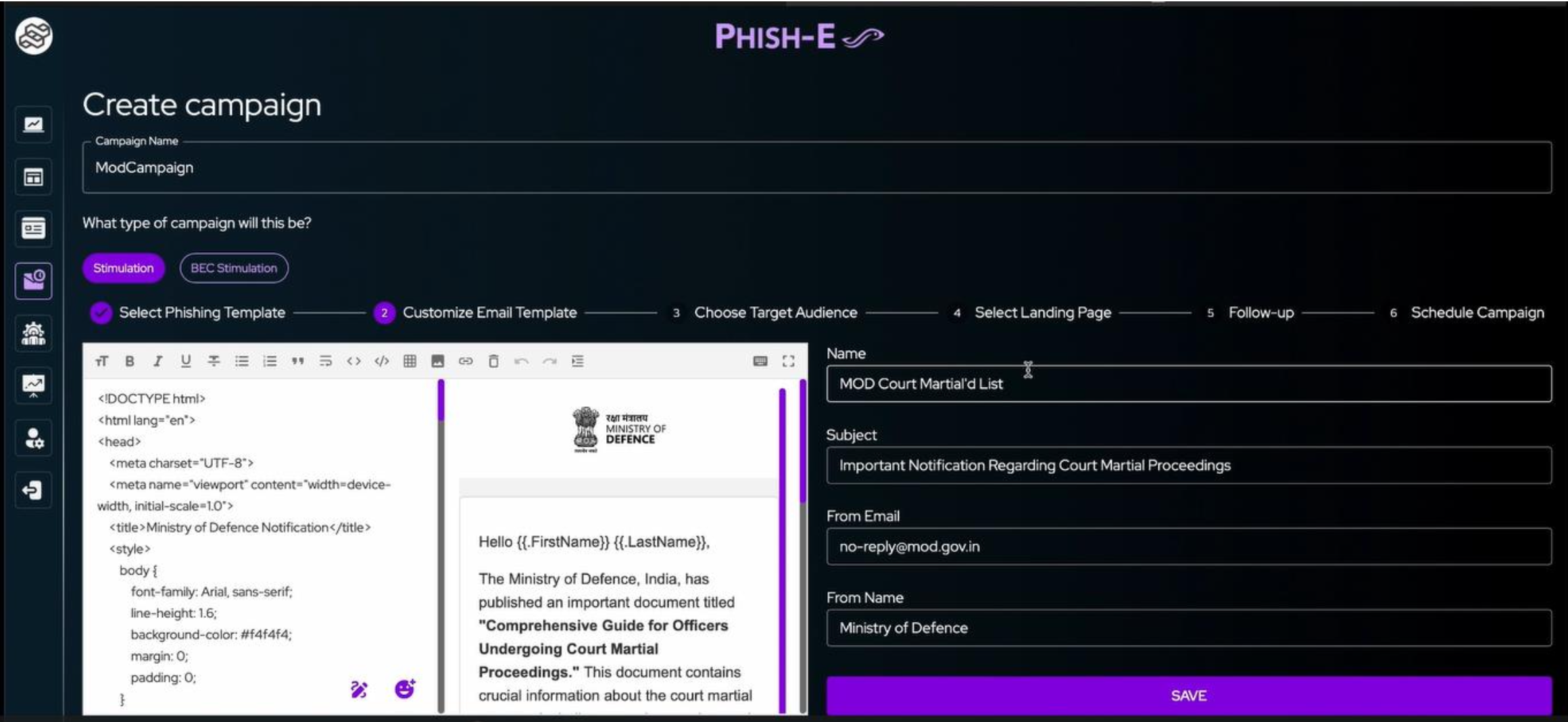
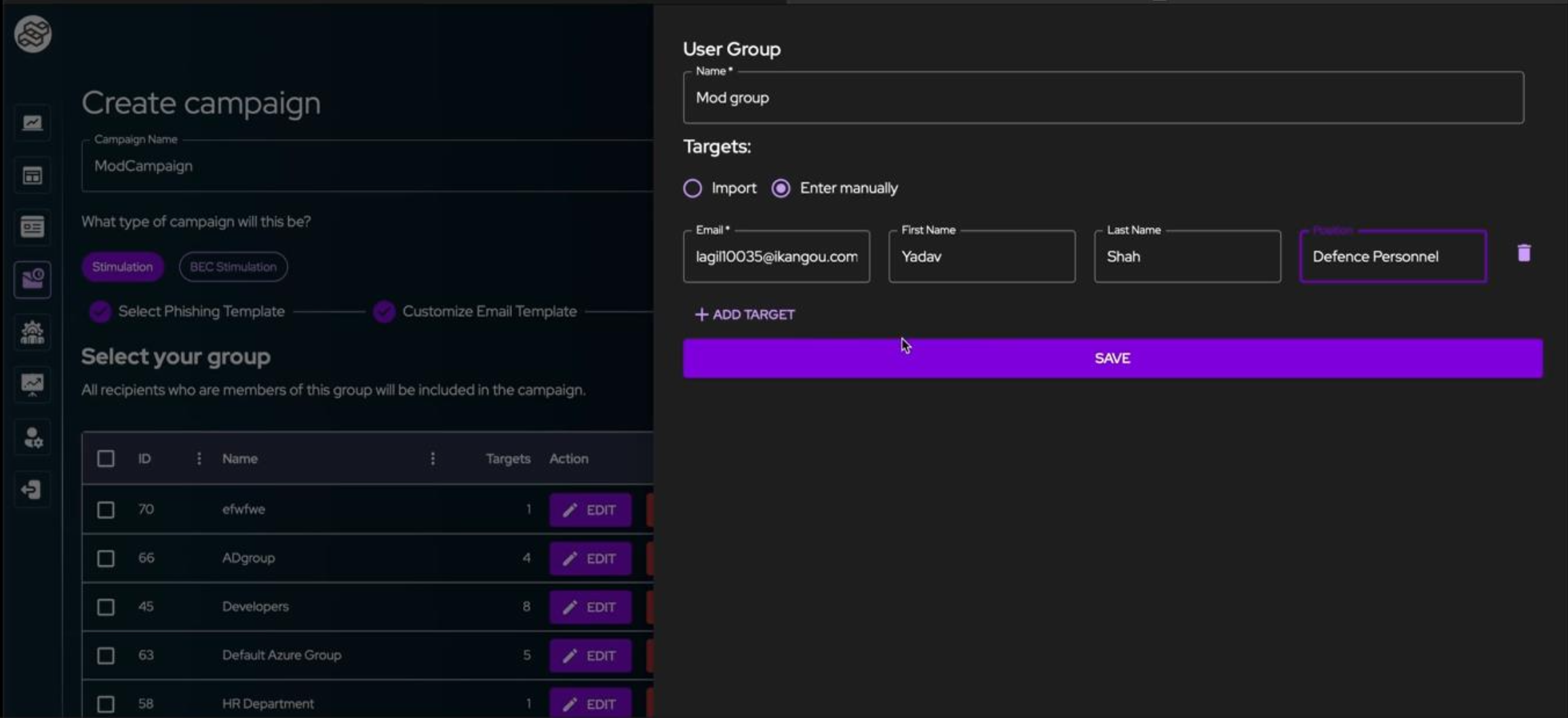
Attackers have a clear understanding of who they are targeting. They spend time sharpening the axe, rather than cutting the tree. SideCopy was aware of the exact targets, and their details like name, official email addresses, online activities, etc.
Before running simulations, create a list of target groups. Organizations use various ways to create target groups like position or level of the employee, departments, non-technical or technical expertise, etc.
Phish-E allows for flexible user group targeting through:
Active Directory Integration: Seamlessly integrate Phish-E with the organization's directory. This reduces the onboarding time and manual effort required to upload employee details.
Import Users: In case, your organization is not using any AD or it isn’t compatible with the tool, we provide an option to upload user details from an Excel or CSV file. The format for the file is available in the tool to download.
Create Individual Users: For small target groups and quick additions, you can manually add users for targeted simulations.
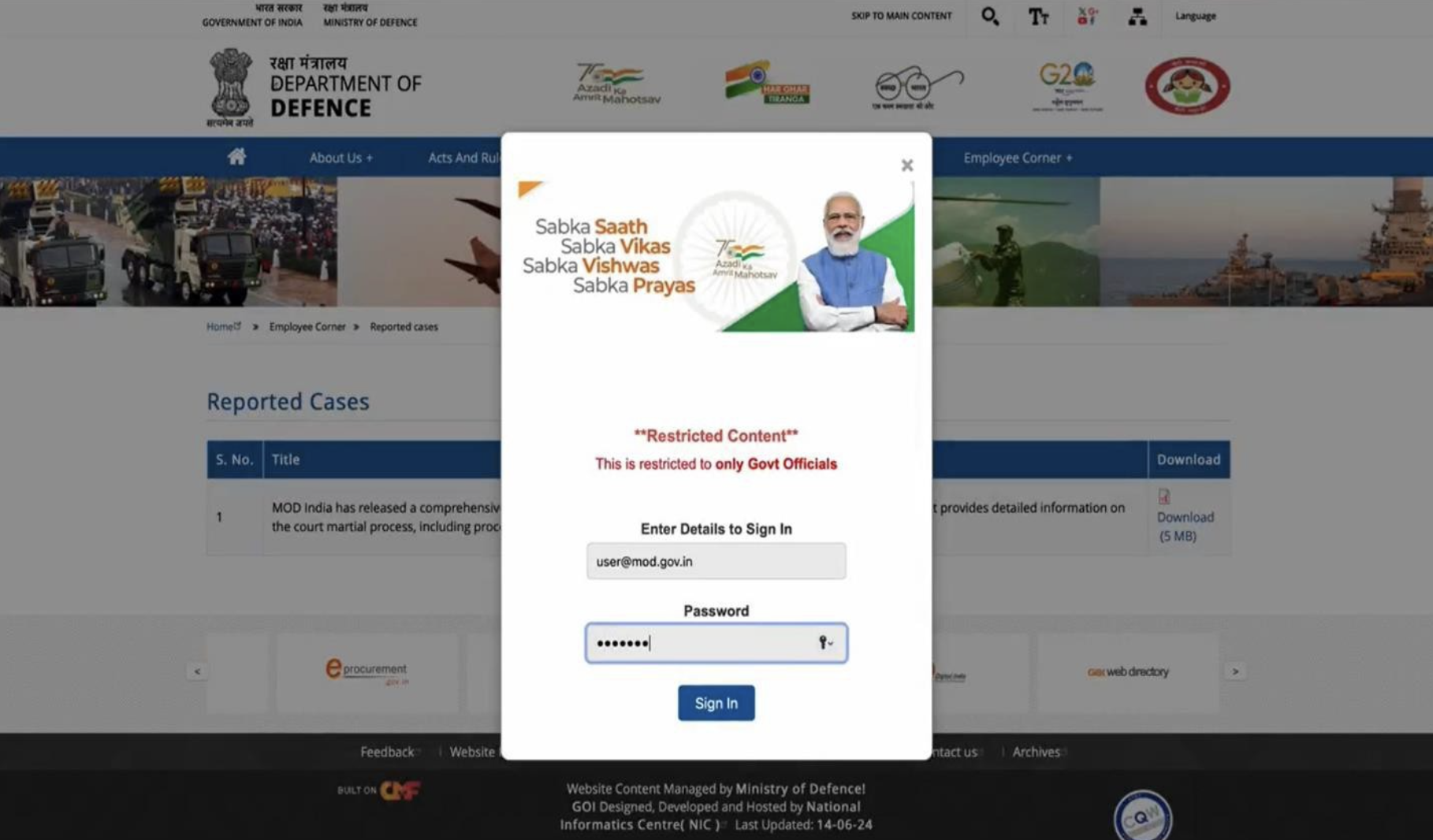
The above landing page was used by SideCopy. It perfectly mirrors the actual landing page of the Ministry of Defence.
A good landing page is created with details. Choose from existing landing pages on popular domains or create a new one using Phish-E's intuitive editor. This page will be where users are redirected to enter their credentials or download malware or whatnot.
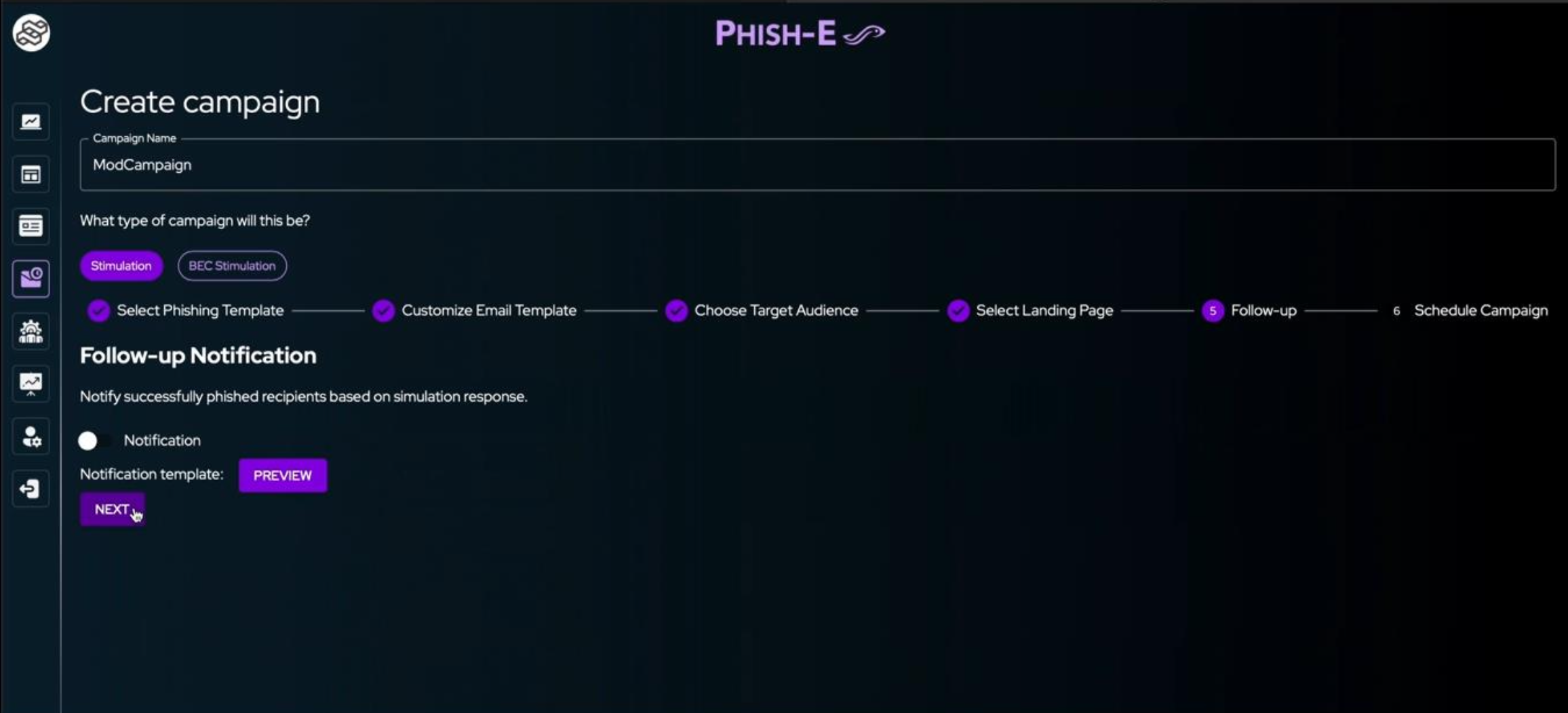
For running a successful phishing simulation, you should notify the users of them being phished. Set up a notification template that will be sent to users who fall for the phishing attempt. This email educates them on their mistake and provides details on the training and steps to be taken in the future.
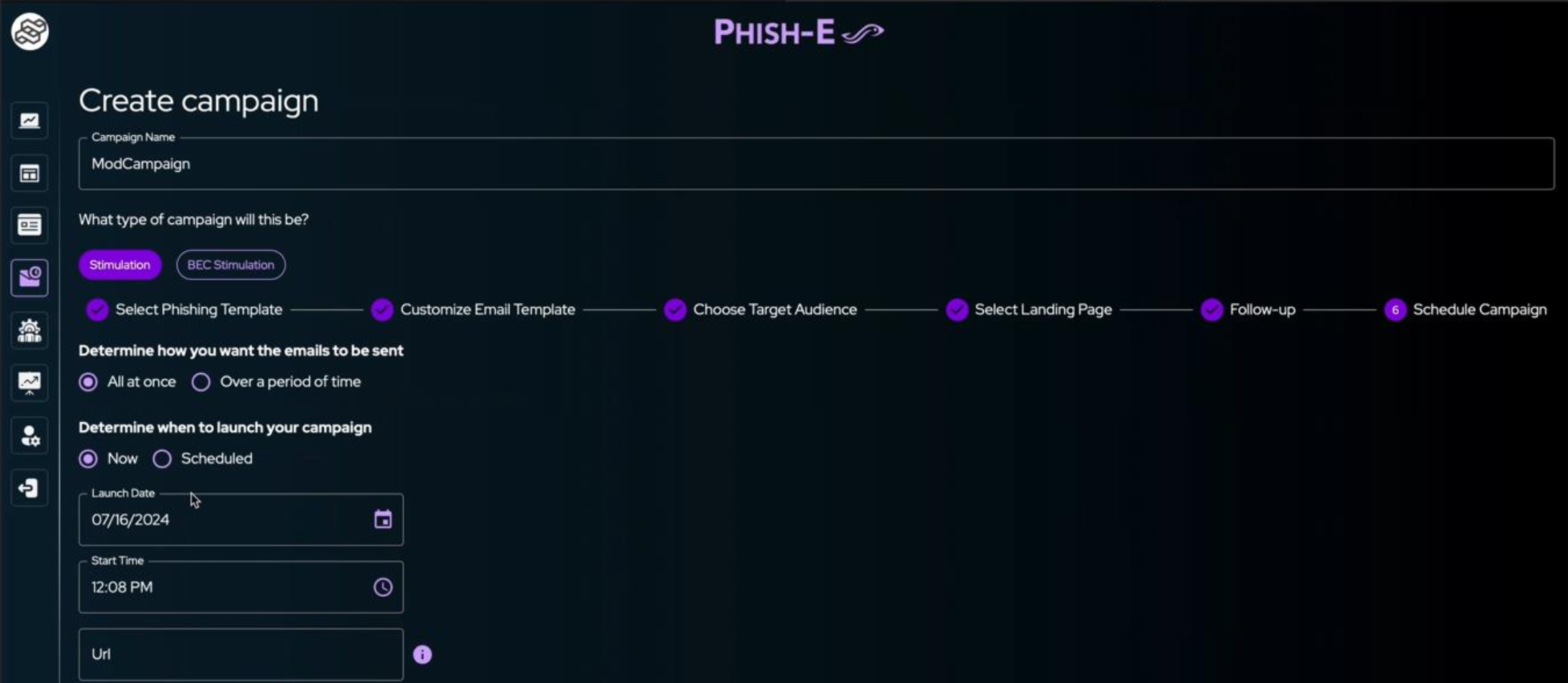
Similar to SideCopy, operators should also know when to run the phishing simulation. It has been observed that users get phished within 60 seconds of them receiving the email. Hence, choosing a time and day to run your simulation is critical.
Phish-E offers flexible scheduling options:
Time is of the essence for attackers. They cannot afford losing out the trail or credentials. Hence, all attackers actively monitor their attacks and observe status in real-time. So why shouldn’t organizations?
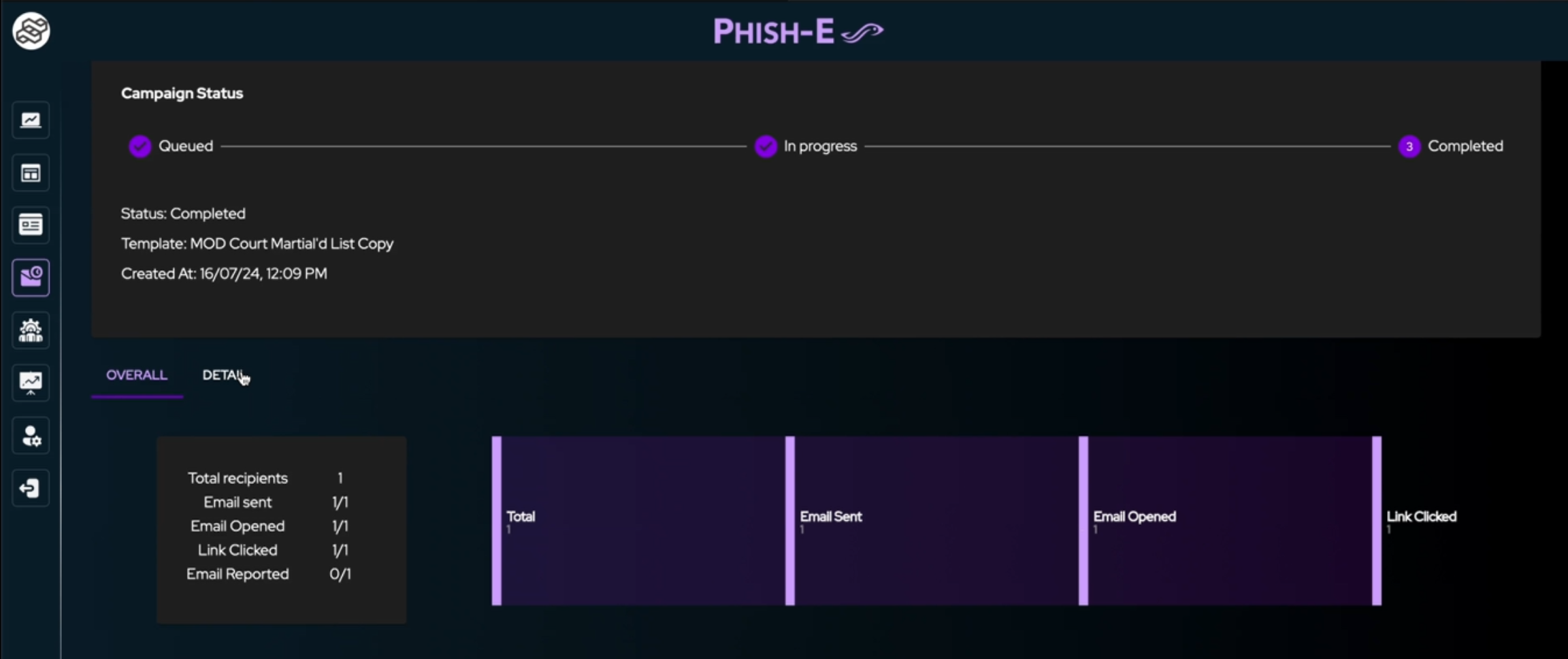
With Phish-E, once launched, the campaign status can be viewed in real-time. The dashboard displays key metrics such as:
Phish-E's dashboard provides real-time data on the simulation's effectiveness. Detailed reports include metrics on user interactions with the phishing email and insights into their susceptibility to such attacks.
Upon launching, the phishing email reaches the target users' inboxes. The email used in the SideCopy simulation created a sense of urgency by urging recipients to check their status on a court-martial list. The fear and urgency prompted users to click on the "verify status" link, leading them to the phishing landing page where they entered their credentials.
Interested in Phish-E? Book a free trial.
Phish-E equips organizations with advanced tools to combat phishing threats by simulating real-life scenarios and training employees to recognize phishing emails. These simulations help in identifying and mitigating vulnerabilities before they can be exploited. Additionally, Phish-E includes a comprehensive cyber resilience program that simulates mass phishing awareness campaigns. These campaigns are highly sophisticated, targeted, and mimic real-world threats to ensure that both the organization and its stakeholders are fully aware of and prepared for these dangers.
Key features include:
Industry-Specific Smart Templates
Phish-E offers templates tailored to various industries, ensuring that simulations are relevant and up-to-date with the latest attack vectors. With smart editing, the tool provides smart templates based on the emotional susceptibility of the target group. You can customize your templates in various sentiments through AI.
AI-Driven Sentiment Analysis
Phish-E uses AI-driven sentiment analysis to identify the emotional triggers in phishing emails. This feature helps create tailored training modules that teach employees to recognize and resist emotional manipulation.
Detailed Reporting and Real-Time Insights
Phish-E provides comprehensive reports that offer real-time insights into employee behavior during simulations. This data helps organizations understand vulnerabilities and improve their cybersecurity strategies.
2FA Bypass Simulation
Attackers often exploit internal mailing software like "Kavach" used by government employees. Phish-E includes 2FA bypass simulations, preparing employees to recognize and counter sophisticated phishing attempts.
The phishing attack on the NIA by SideCopy highlights the critical need for robust cybersecurity measures. Phishing simulations with tools like Phish-E play a vital role in preparing organizations for real-world threats. By continuously updating templates, leveraging AI for sentiment analysis, and providing detailed reporting, Phish-E ensures that employees are well-equipped to recognize and respond to phishing attempts, safeguarding sensitive information and national security.




