Vulnerability Assessment and Penetration Testing (VAPT)
In today’s ever-evolving digital landscape, Vulnerability Assessment and Penetration Testing (VAPT) plays a critical role in identifying and mitigating security risks. With cyberattacks becoming more sophisticated and widespread, organizations need a proactive approach to safeguard their assets. P.I.V.O.T Security offers world-class VAPT services, combining two core activities—Vulnerability Assessment (VA) and Penetration Testing (PT)—into a unified security process.
What is VAPT?
VAPT stands for Vulnerability Assessment and Penetration Testing, a systematic approach to evaluating an organization’s security posture by identifying, prioritizing, and addressing vulnerabilities in its infrastructure. With P.I.V.O.T Security, you gain access to highly skilled security experts who mimic hacker tactics to uncover security gaps, ensuring your organization is always a step ahead of attackers.
VAPT provides both detection (vulnerability assessment) and defense (penetration testing), ensuring that your organization remains compliant with industry standards and secure from cyber threats. P.I.V.O.T Security helps you identify vulnerabilities and implement effective remediation strategies, securing your organization’s infrastructure before attackers find their way in.

The Difference Between Vulnerability Assessment and Penetration Testing
While both Vulnerability Assessment (VA) and Penetration Testing (PT) are key components of P.I.V.O.T Security's VAPT services, they serve distinct purposes:
- Vulnerability Assessment is a systematic evaluation of security weaknesses. It focuses on identifying known vulnerabilities and providing recommendations for remediation.
- Penetration Testing, on the other hand, involves actively exploiting vulnerabilities to simulate real-world attacks. P.I.V.O.T Security’s penetration testers provide detailed insights into how far an attacker could penetrate the system.
| Feature | Vulnerability Assessment | Penetration Testing |
|---|
| Goal | Identify potential vulnerabilities | Exploit vulnerabilities to assess impact |
| Methodology | Automated scans | Manual offensive attack simulation |
| Scope | Surface-level scans | In-depth exploration of business logic |
| Frequency | Weekly or monthly | Quarterly or annually |
| Compliance | Helps prepare for compliance | Often necessary for compliance standards |

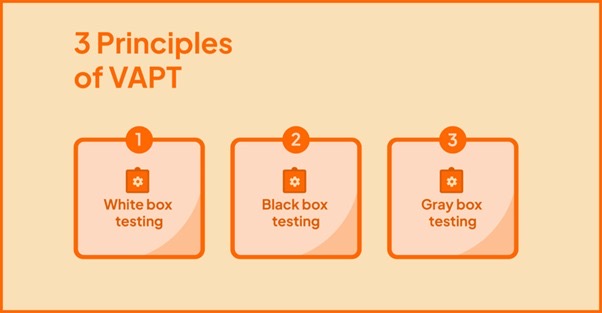
Principles of VAPT: Black, White, and Gray Box Testing
At P.I.V.O.T Security, VAPT assessments can be categorized into three types based on the amount of information provided to the tester:
- Black Box Testing: Testers have no prior knowledge of the system, simulating an external attack.
- White Box Testing: Testers are given full access to the system’s architecture and source code, allowing a deep exploration of vulnerabilities.
- Gray Box Testing: A hybrid approach where testers have partial access to the system, simulating an insider threat with some internal knowledge.
Why VAPT is Essential: Benefits and Real-World Examples
With the increasing number of data breaches and cyberattacks, VAPT is crucial for organizations to secure their sensitive data. P.I.V.O.T Security offers VAPT services that are tailored to help you:
- Leverage Comprehensive Evaluation: Identify both known and unknown vulnerabilities, ensuring all potential attack vectors are covered. For instance, recent data breaches in India exposed millions of users' accounts, a scenario that could have been prevented through regular VAPT.
- Adopt a Security-First Approach: VAPT allows organizations to be proactive, identifying and fixing vulnerabilities before attackers exploit them. An example of this is the BeerBiceps hack, where a prominent YouTuber lost control of his channels. With proper VAPT, the security flaws leading to this breach could have been identified early.
- Stay Compliant: VAPT is a crucial part of regulatory compliance for frameworks like GDPR, HIPAA, and PCI-DSS. It ensures that businesses meet security standards, protecting customer data and building trust.
- Build Trust with Stakeholders: A strong security posture signals to customers, partners, and investors that your organization is committed to protecting sensitive data, thus enhancing your reputation.

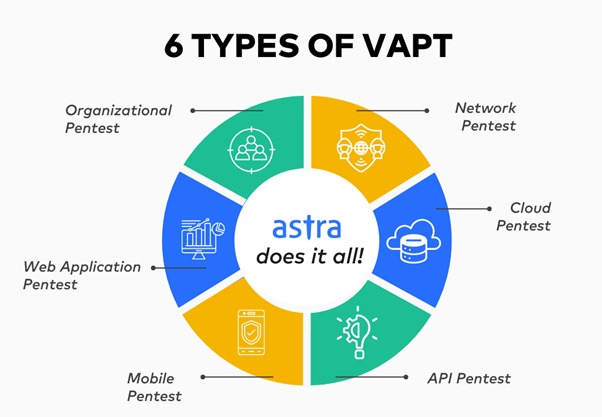
Types of VAPT Assessments by P.I.V.O.T Security
P.I.V.O.T Security offers VAPT services for various components of an organization’s infrastructure, ensuring comprehensive security coverage:
- Network Security: This involves identifying vulnerabilities within internal and external networks, ensuring that the infrastructure is not vulnerable to unauthorized access.
- Web Application Security: In this type of assessment, we focus on identifying and mitigating vulnerabilities in web applications such as SQL Injection, Cross-Site Scripting (XSS), and broken authentication mechanisms.
- Mobile Application Security: P.I.V.O.T Security evaluates the security of mobile apps, identifying flaws such as insecure data storage, reverse engineering, and weak authentication processes.
- Cloud Security: As cloud services become more prevalent, P.I.V.O.T Security assesses cloud environments to uncover misconfigurations, insecure APIs, and weak access controls that could lead to data breaches.
- API Security: Application Programming Interfaces (APIs) are critical components of modern applications. Our team tests APIs to ensure they are not vulnerable to attacks like Insecure Direct Object References (IDOR) or injection flaws.
- Wireless Security: Wireless networks are often targeted by attackers due to weak encryption or improper configuration. P.I.V.O.T Security tests these networks to prevent unauthorized access.
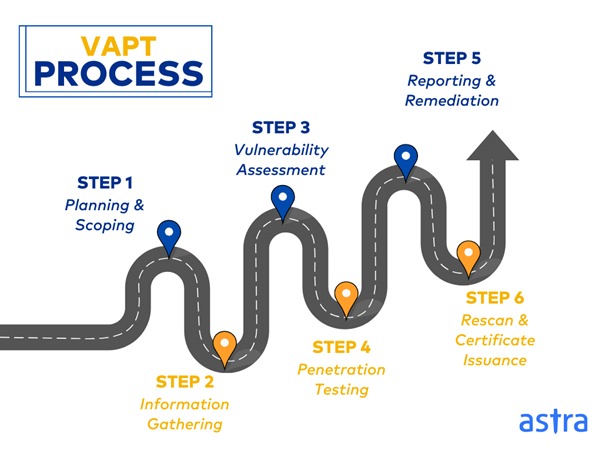
The VAPT Process at P.I.V.O.T Security
At P.I.V.O.T Security, the VAPT process is thorough and follows six key steps:
- Planning and Scoping: Define the scope of the assessment, including the assets to be tested and the type of testing (black, white, or gray box).
- Information Gathering: Collect detailed information about the target infrastructure.
- Vulnerability Assessment: Use both automated tools and manual techniques to identify potential vulnerabilities.
- Penetration Testing: Attempt to exploit the identified vulnerabilities to understand the real-world impact of a cyberattack.
- Reporting and Remediation: Document findings, including recommendations for fixing the vulnerabilities.
- Rescan and VAPT Certificate Issuance: Perform a final scan to ensure all issues have been resolved and issue a VAPT certificate.
How to Choose the Right VAPT Provider
When selecting a VAPT provider, it is essential to partner with a trusted name like P.I.V.O.T Security. Here’s what sets P.I.V.O.T Security apart:
- Understand Your Needs: We tailor our services to meet your specific business needs, ensuring comprehensive assessments that address all potential risks.
- Methodological Depth: P.I.V.O.T Security follows established industry standards like OWASP and PTES to ensure that every possible attack vector is tested.
- Transparent Communication: We provide regular updates and clear explanations of our findings, making the remediation process smooth and collaborative.
- Experience and Certifications: Our team consists of certified experts with proven experience in VAPT across various industries. We ensure that your security is in the best hands.
References:
- Sprinto "VAPT in Cyber Security" Sprinto Blog.
- Astra Security "What is VAPT?" Astra Blog.
- Craw Security "Understanding Vulnerability Assessment and Penetration Testing (VAPT)" Medium.
- Hindustan Times "Ranveer Allahbadia's YouTube Channels Hacked" Hindustan Times.




