

Crafting resilient defenses is essential in protecting against a growing number of malicious threats. Organizations across the globe invest significantly in defensive solutions, relying on their capabilities to detect and block adversaries. Adversaries and defenders are engaged in an ongoing cat-and-mouse game and as defenders devise new protection strategies, attackers simultaneously innovate novel ways to circumvent these defenses. At P.I.V.O.T Security, we believe that understanding the intricacies of these bypass techniques is essential for maintaining robust defense.
Alright, straight from the P.I.V.O.T's R&D red team labs:
We've brainstormed and conceptualized an intriguing new technique - Bring Your Own Reputation (BYOR). A recent demonstration of this was made on our LinkedIn post where we showcased a video of BYOR technique.
POC - With BYOR Bypass: This technique ensured there were no SmartScreen prompts and Windows Defender (WD) remained silent to our exploitation attempts.
To begin the process, we first set up a Havoc Command & Control server on a VPS, which enabled us to access it remotely using a Team server to access the GUI. Once Havoc was set up, we created a custom payload that would allow us to get the callback inside Havoc, which paves the way for our BYOR technique.
A foundational understanding of any system is the key to navigating its complexities and Microsoft's SmartScreen is no exception. Let's take a closer look at how SmartScreen operates. According to Microsoft Microsoft Defender SmartScreen identifies potentially malicious downloaded apps or installers in two primary ways:
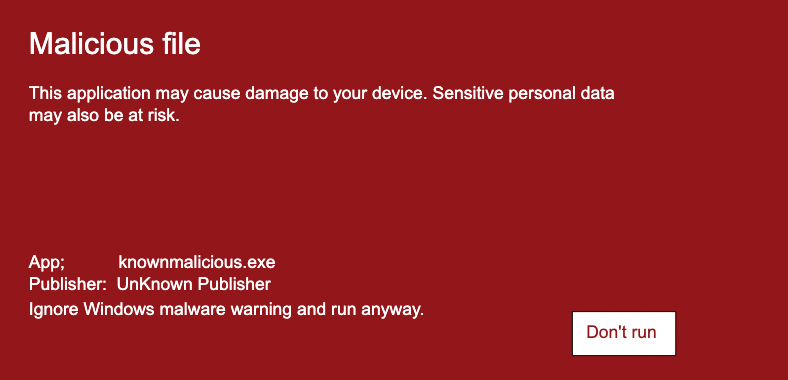
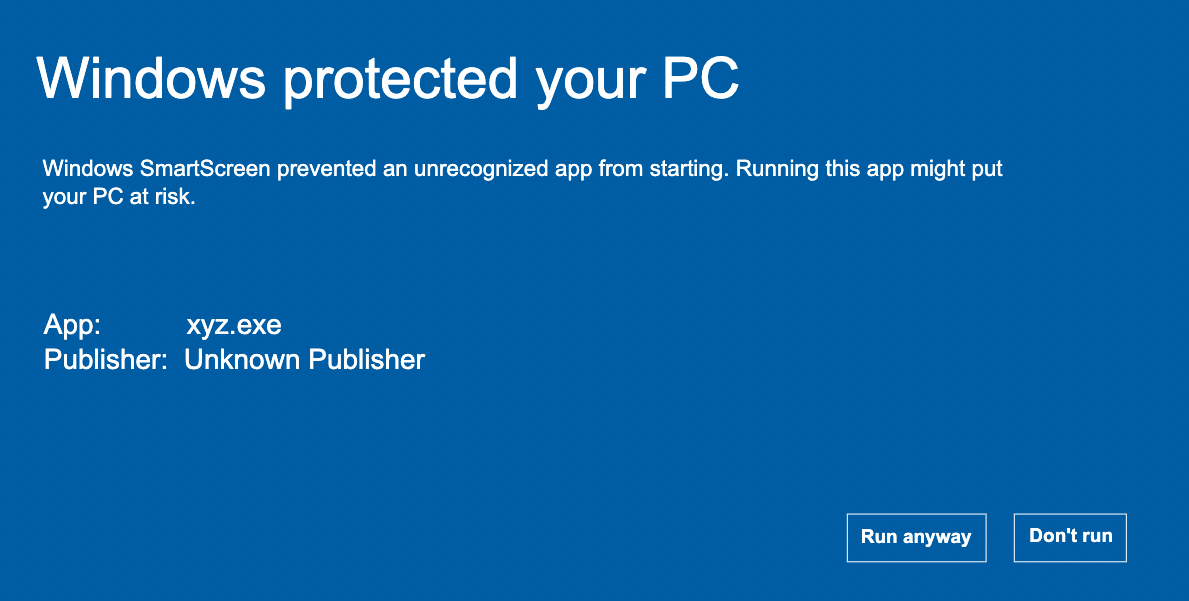
It carefully inspects downloaded files, comparing them against an extensive list of reported malicious software sites and programs. If there's any match then a warning pops up which signals the user about the potential harm.
Parallelly, it evaluates these files against a list of popular and frequently downloaded items. If a particular file hasn't made its mark on this list, the SmartScreen raises an alert which suggests the user to proceed with care.
Windows, like many operating systems has multiple lines of defense to protect its users. One notable feature is SmartScreen which uses cloud-based anti-phishing and anti-malware components to check web pages and files against a list of reported malicious sites and files. To enhance this security feature, any file downloaded from the internet is tagged with the Mark of the Web (MOTW), acting as a footprint of the file's origin.
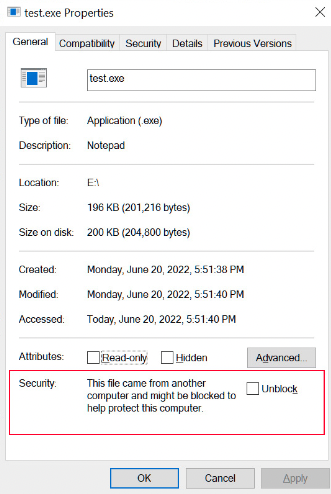
This system is mostly reputation-based which means that well-known files with a positive track record are less likely to be flagged or restricted. Windows' reputation-based system, as mentioned, will generally trust files that are well-known and have previously been deemed safe. The potential loophole could arise in how this "reputation" is determined or manipulated.
To shed some light on the current exploitation techniques used by threat actors, lets look at them first.
To fully appreciate the potential of the BYOR technique, it's essential to understand the current strategies threat actors employ to bypass systems like SmartScreen:
Signed Executables: Files like Exe, MSI, MSIX, APPX, or even 'click once' applications are often signed to help bypass security measures. However, many of these methods require an extra EV certificate to bypass SmartScreen, making it a restrictive path for numerous threat actors.
Containerizing the Initial Infection: Some adversaries use containers such as zip, iso, vhdx, vhd, or 7z to wrap the payload, intending to bypass browser protection. But this method still faces challenges with MOTW/SmartScreen.
ISO with Sideloading: Using ISO sideloading can effectively bypass SmartScreen checks and execute payloads. Yet, this method's popularity means it's more likely to be detected by EDR systems.
This brings us to the core question:
Can BYOR truly overcome these challenges ?
But here's where things get interesting. What if hypothetically, one could manipulate or make use of files already in Microsoft's "good list"? Could we then be able to trick SmartScreen and bypass the security checklist?
A prevalent myth exists that for an .exe, .dll, or even an .msi to gain Microsoft's stamp of approval, it needs to bear a EV signature. But our hands-on research paints a different picture. In our studies, we've encountered numerous executable files .exe, .msi etc. that successfully evaded SmartScreen's checks, despite lacking a valid digital signature.
When software accumulates a substantial number of downloads, it steadily establishes a positive Smartscreen reputation. And this very reputation mechanism is what we're keen on exploring further with BYOR technique.
Bring Your Own Reputation (BYOR) is old and lesser known bypass technique which is being conceptualized to exploit the inherent reputation-based system of defenses such as Microsoft's SmartScreen. The core philosophy behind BYOR stems from understanding that many modern protective measures notably SmartScreen, lean on the reputation of files to determine their safety.
Exploitation of Reputation Mechanism: At its heart, BYOR is about understanding and manipulating the reputation mechanism.
Beyond Signatures: Unlike some other bypass methods which require files to have a digital signature, BYOR operates beyond this. In the BYOR approach, files that lack a valid digital signature but have an established reputation can still bypass checks.
Microsoft's Smartscreen is designed to swiftly verify whether a downloaded executable or a browsed site is recognized as safe or harmful. Our main aim is centered on optimizing our initial access delivery.
When Smartscreen scans a file before saving it to disk, it checks if the downloaded file is recognized as safe. If it's identified as a widely downloaded and safe file, it allows the download. However, if the file is unfamiliar or has been flagged as malicious, the user sees a stringent Smartscreen warning.
With bypass techniques like CVE-2022-44698 emerging, threat actors consistently devise new methods. The term "Bring Your Own Reputation" (BYOR) defines a category of files (both signed and unsigned) that are whitelisted by SmartScreen and can be manipulated to evade security measures.
BYOR encompasses various file types including .bat, .jscript, .vbscript, .msi, and .exe, which can be leveraged to bypass checks.
While digital signatures are a standard method for establishing trust, they're not the only one. Remember, reputation-based systems, by their nature, lean on the historical behavior of files. If a file has been widely circulated, used, and hasn't been flagged as malicious over time, it could gain a positive reputation.
Wondering how to implement BYOR to your advantage? If we mirror the strategies utilized in DLL sideloading, we can curate a similar sequence via BYOR which opens the door for unsigned sideloading as well. Let's illustrate the process we showcased in our LinkedIn post with a straightforward flowchart for better clarity:
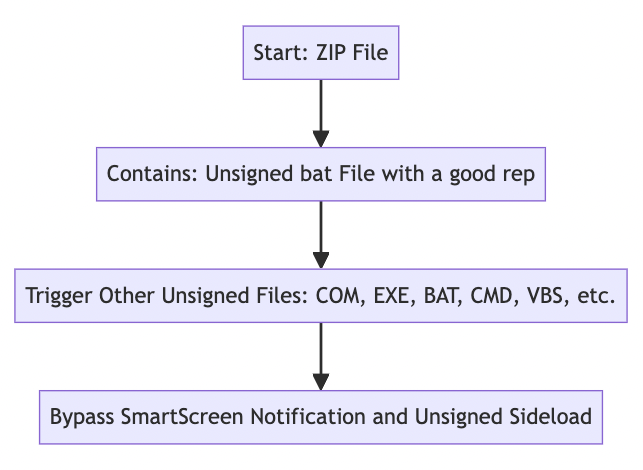
Let's delve into how this method can be utilized for creating an initial access chain using a simple yet effective example.
Find a Reputed file which is badly coded.
Locate A Source to Download Such Files
Choosing the Right File
Exploitation Strategy
Diving into the Chosen File


Taking Advantage of the Flaw
Crafting the Initial Access Chain & Testing It
For delivery purposes, we created a .zip file using our in-house (in-research) OCA (Offensive Chain by Astra) framework. With OCA we are automatically able to create a BYOR payload with just a few clicks, saving us a huge amount of time and making the jobs of red teamers more efficient to test their organization infrastructure with new kill chains. A standout feature includes the ability to auto-deploy the crafted payload to a designated VPS for hosting as demo'ed in this post. Within the zip which is stored securely on VPS, there are two crucial files: a BYOR-driven batch file capable of evading both MOTW (Mark of the Web) and SmartScreen, along with an unsigned sideloaded executable. We are excited to share that the initial version v0.1 will soon be available, providing red teamers with a powerful tool to assess their organization's defenses.
We plan to release a more comprehensive version focusing on evasive loaders in an upcoming post.
BYOR offers unique advantages in sideloading. Some innovative techniques to enhance outcomes include:
The OCA (Offensive Chains by Astra) framework offers a unique methodology to bypass browser security policies and advanced endpoint defenses. By integrating the above sideloading technique with the OCA framework, we can successfully pwn most of the Endpoint Detection and Response (EDR) backed host. In our tests, we enhanced the sideloading approach using the OCA framework by combining it with various other methods (BYOR gadgeting :D), resulting in a more powerful attack simulation strategy.
At its core, BYOR Gadgeting refers to the strategic use of trusted and legitimate code or functionalities ("gadgets") within reputable software. Inside an organization red teamers can harness these gadgets to simulate potential attack vectors, highlighting that even trustworthy software can be manipulated. This method can be more stealthy and harder to detect because security systems are often designed to detect and block known malicious code or suspicious behaviors but they may not be as effective in spotting the misuse of legitimate functionalities.

Our in-house developed OST called "Offensive Chains by Astra" demonstration can be seen below utilizing BYOR technique: If you are interested in watching the PoC for the BYOR generated payload, you can skip to the end of the article.
For the time being we are only supporting windows, but we plan to release and support other operating system like linux and macOS in near future.
The primary aim is to mimic a real-world attack and emulate the tools, techniques, and procedures (TTPs) of actual threat actors to expose weaknesses. With our innovative OCA (Offensive Chains by Astra), we’re not just meeting the industry standards but taking a leap forward.
Conventionally, when assessing an organization's security posture, it's common to simulate known attacks or kill chains. The idea is simple: by understanding how defenses hold up against recognized threats organizations can design strategies to stop them. This simulation results in creating a 'playbook' which serves as a defense manual against such known cyber-attacks.
However, we believe that for truly robust security, we must go beyond what's already known. Here's where the OCA Framework stands out. While it's beneficial to have a playbook against recognized attacks it's equally important to acknowledge that in real-world scenarios, when an organization comes under a targeted attack, these playbooks might not work as expected.
So it's crucial to test infrastructure defenses against the latest cyber offense techniques that are not yet in the limelight. These lesser-known vectors which may not be widely abused yet have the potential to be the next large-scale breach.
Our OST deeply integrate this principle. We prioritize researching such understudied vectors, understanding their potential risks and incorporating them into our simulation techniques.
BYOR, as a concept carries vast implications for the world of cybersecurity. It indicates that even software considered safe might have its own flaws. As the digital landscape grows, the list of trusted software also expands which gives attackers more opportunities to exploit. This means that one should evaluate their infrastructure defenses using the most recent cyber-attack techniques including those that are not widely recognized or exploited.
The trajectory of cybersecurity is determined by the community. Depending on the direction the community wishes to pursue regarding BYOR and similar tactics ... we're determined to share further insights, detection mechanisms and offensive techniques.
The insights we've provided here are just the tip of the iceberg. At P.I.V.O.T Security we possess a wide range of strategies and we're excited to uncover them in our future articles.
In essence, Cybersecurity is about staying ahead of the curve. With challenges like BYOR popping up we also discover new defenses. As we continue this path - teamwork, innovation and knowledge sharing are key. And as always remember:
The best way to predict the threat landscape is to create it.




