
July 2024 has been a watershed month for cybersecurity, with three major breaches dominating the headlines and shaking the business world to its core. Businesses scrambled to manage disruptions, consumers worried about the security of their personal data, and social media became a battleground for frustration and, in some cases, humor.
In our digital age, staying updated on cybersecurity threats and significant tech events is crucial. The incidents in July 2024 caused considerable upheaval in the industry, sparking lively discussions and reactions on platforms like LinkedIn and Twitter.
In this comprehensive analysis, we’ll dissect each event, examining their backgrounds, impacts, and the lessons they offer. Our goal is to provide businesses with a clear, insightful guide to bolstering their cybersecurity defenses. Join us as we navigate these incidents with a knowledgeable and informed lens.

In a shocking revelation that has sent ripples through the business and cybersecurity communities, Disney is investigating a significant data leak after hackers posted alleged internal communications online. The hacker group Nullbulge claims to have obtained and leaked more than 1 terabyte of data from Disney’s internal Slack channels. Social media platforms erupted with reactions to the breach. Hashtags like #DisneyHack and #Nullbulge trended, with users expressing a mix of shock, concern, and schadenfreude. Cybersecurity experts weighed in on the implications, while Disney fans and critics debated the company’s handling of the situation. The incident underscores the increasing sophistication and audacity of cybercriminals, and it serves as a stark reminder of the vulnerabilities even the largest and most secure organizations face.
The attack targeted Disney's internal Slack channels, a critical communication tool for the company's operations. Nullbulge, a notorious hacker group which claimed responsibility for the breach. Nullbulge known for sophisticated techniques and previous high-profile attacks, managed to infiltrate Disney's internal communication network and exfiltrate sensitive data.
In July 2024, Nullbulge announced they had successfully hacked into Disney's Slack channels, accessing over 1 terabyte of internal communications. They leaked this data online, exposing sensitive information and internal discussions. The leaked data incorporated confidential conversations, strategic plans, and personal employee information. The breach's impact was immediately felt, causing operational disruptions and significant reputational damage to Disney.
The breach was publicly disclosed in mid-July 2024, but the exact timeline of the infiltration is still under investigation. Initial reports suggest that the attackers might have had access to Disney's Slack channels for several weeks before the breach was detected and made public.
The accurate technique used by Nullbulge remains unclear, but cybersecurity experts believe the attack involved sophisticated phishing techniques and exploiting vulnerabilities in Slack’s security protocols. It's likely that the attackers gained access through compromised employee credentials, which allowed them to navigate Disney's internal network undetected.
The motive behind the attack appears to be multifaceted. Nullbulge has a history of targeting high-profile companies to demonstrate their hacking capabilities and possibly for financial gain through extortion or selling sensitive data on the dark web. Additionally, such breaches can serve to disrupt business operations and damage corporate reputations.
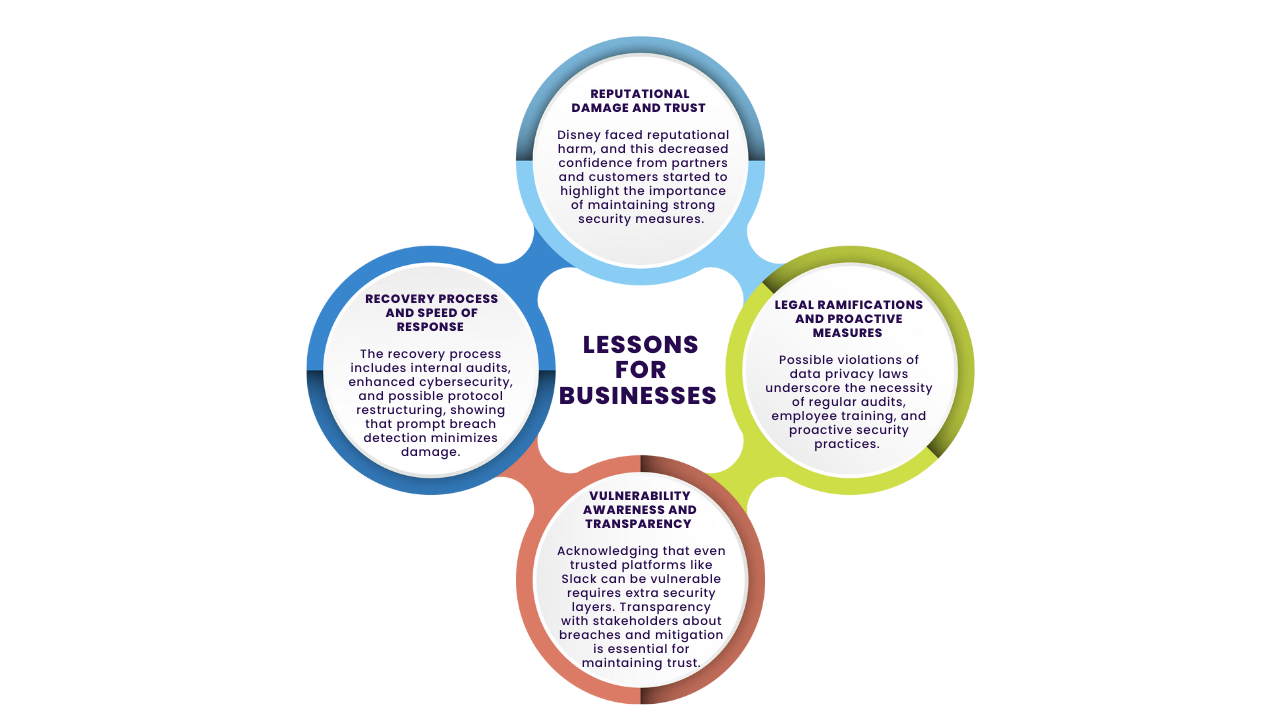
The immediate fallout from this breach has been significant. Disney’s stock experienced a notable dip as investors reacted to the news. The leak has also disrupted internal operations as employees and management scramble to assess the extent of the breach and mitigate any potential damage. Moreover, the exposed internal communications may contain sensitive information that could compromise business strategies and negotiations.
Preventing such breaches requires a multi-faceted approach to cybersecurity. Enhanced security protocols are essential, including the implementation of robust measures for internal communication platforms, such as end-to-end encryption and multi-factor authentication. Regular security audits must be conducted frequently and thoroughly to identify and rectify vulnerabilities before they can be exploited. Employee training is also crucial and regular sessions should be held to educate staff on recognizing and avoiding phishing attempts and other social engineering tactics. Additionally, developing and maintaining comprehensive incident response plans is vital to quickly address and contain any breaches that occur.

In the dynamic world of cybersecurity, the events of July 2024 serve as a stark reminder of the vulnerabilities inherent in our digital infrastructure. A routine update from Crowdstrike, typically seen as a necessary measure to enhance security and functionality, became the catalyst for a major BSOD outage on Windows systems that rippled across global businesses. This incident, now referred to as the "July 2024 Windows Update Glitch," highlighted the precarious balance between maintaining system availability through updates and the potential risks these updates can introduce.
The glitch manifested through a faulty update that inadvertently opened loopholes in the Windows operating system. The severity of the incident was underscored by its timing; many organizations were unprepared for the sudden unavailability of systems, resulting in a significant impact on business operations, data integrity, and overall trust in software updates.
Interestingly, this major incident was not the result of a cyberattack. There were no malicious actors breaching defenses or exploiting vulnerabilities. Instead, it was a self-inflicted wound, stemming from a configuration update error. The absence of an external attacker, however, did little to mitigate the damage experienced by businesses relying on the affected systems.
The incident impacted systems running the Falcon sensor for Windows version 7.11 and above. The affected Channel File, identified as 291, controlled how Falcon evaluated named pipe executions on Windows systems. Named pipes, integral for interprocess communication, were being updated to counter newly observed malicious uses. Unfortunately, the update’s logic error triggered system failures instead.
The glitch occurred on July 19, 2024, when the problematic configuration update was released. The issue was identified and remediated on the same day. Although the timeframe was relatively short, the impact was widespread due to the critical nature of the systems involved and the global reach of the Falcon platform.
The root cause of the incident was a logic error within Channel File 291. This file, responsible for evaluating named pipe executions, was intended to bolster defenses against new cyberattack methods. However, the update contained an unforeseen error, leading to system crashes. Despite rigorous testing and quality assurance processes, this error slipped through, demonstrating that even the most stringent safeguards can sometimes fail.
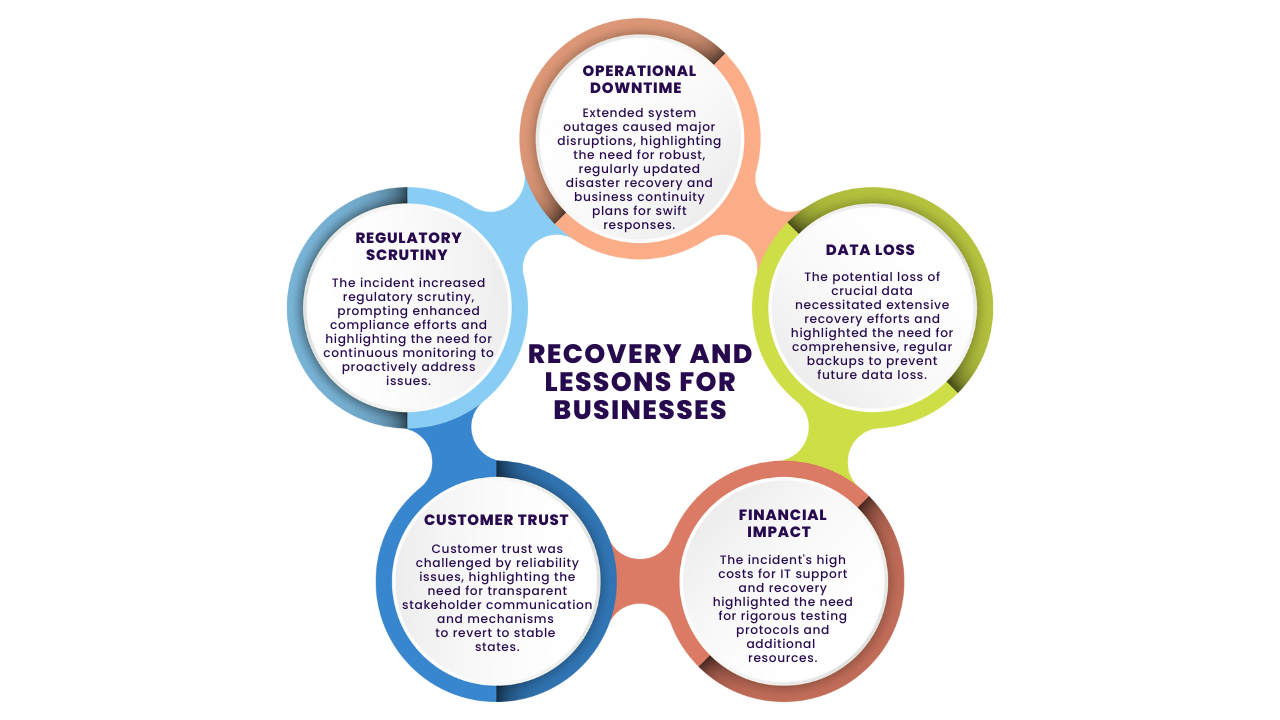
The immediate impact on businesses was significant. Systems crashed, leading to disruptions in operations, delays in business processes, and potential data loss. For many companies, the BSOD is synonymous with halted productivity and emergency IT interventions. The incident highlighted the dependence on reliable update mechanisms and the fragility of digital infrastructure in the face of unexpected failures.
Preventing such incidents involves a multi-faceted approach. Firstly, implementing more rigorous testing protocols, including stress tests and simulations of potential errors, could help identify issues before deployment. Secondly, establishing a rollback mechanism for updates can quickly revert to a stable state if problems arise. Thirdly, continuous communication with affected businesses during an incident can help manage the situation more effectively and maintain trust.

In July 2024, AT&T, one of the world's leading telecommunications companies, faced a significant data breach that sent shockwaves through the business community. With nearly 74 million customers affected, sensitive information such as names, addresses, social security numbers, and financial details were compromised, sending shockwaves through the business community and beyond. The breach didn't just affect the company’s bottom line, it also raised urgent concerns about data security and consumer privacy on a grand scale.
Social media platforms buzzed with outrage and concern as users reacted to the news and many expressed their frustration over AT&T's apparent failure to safeguard customer records, which lead to demanding accountability and stronger protective measures. The hashtags #ATTDataBreach and #DataPrivacy quickly gained traction, illustrating a growing awareness and concern about the security of personal data in an age where breaches have become all too common.
The AT&T data breach, which surfaced in mid-July 2024, was orchestrated by a sophisticated group of cybercriminals. The breach was detected by AT&T's security team, who noticed unusual activity in their data servers located in Texas.
In this breach, the attackers infiltrated AT&T's customer database, gaining access to personal information, including names, addresses, social security numbers, and financial details of nearly 110 million customers. The breach not only compromised sensitive data but also exposed AT&T's internal systems to potential manipulation, raising concerns about the integrity of their communication infrastructure.
The breach occurred over a period of several weeks, with the initial infiltration detected on July 5, 2024, but investigations revealed that the initial intrusion occurred as early as June 25, 2024. However, it wasn't until July 18, 2024, that AT&T publicly acknowledged the breach after realizing the full extent of the damage.
The attackers used a multi-vector approach, combining spear-phishing emails targeting AT&T employees with sophisticated malware that exploited a zero-day vulnerability in the company's customer management system. This malware, designed to remain undetected, provided the attackers with a backdoor into the system, enabling them to siphon data over an extended period.
The motives behind the attack appear to be both financial and strategic. The stolen data can be sold on the dark web, potentially fetching millions of dollars. Additionally, the breach serves as a demonstration of the attackers' capabilities, potentially positioning them for future, more lucrative contracts within the cybercriminal underworld.
The immediate fallout from the AT&T breach has been severe. Customers, wary of potential identity theft and fraud, have inundated AT&T with inquiries and requests for enhanced security measures. The breach has also triggered a significant drop in AT&T's stock value, reflecting diminished investor confidence.
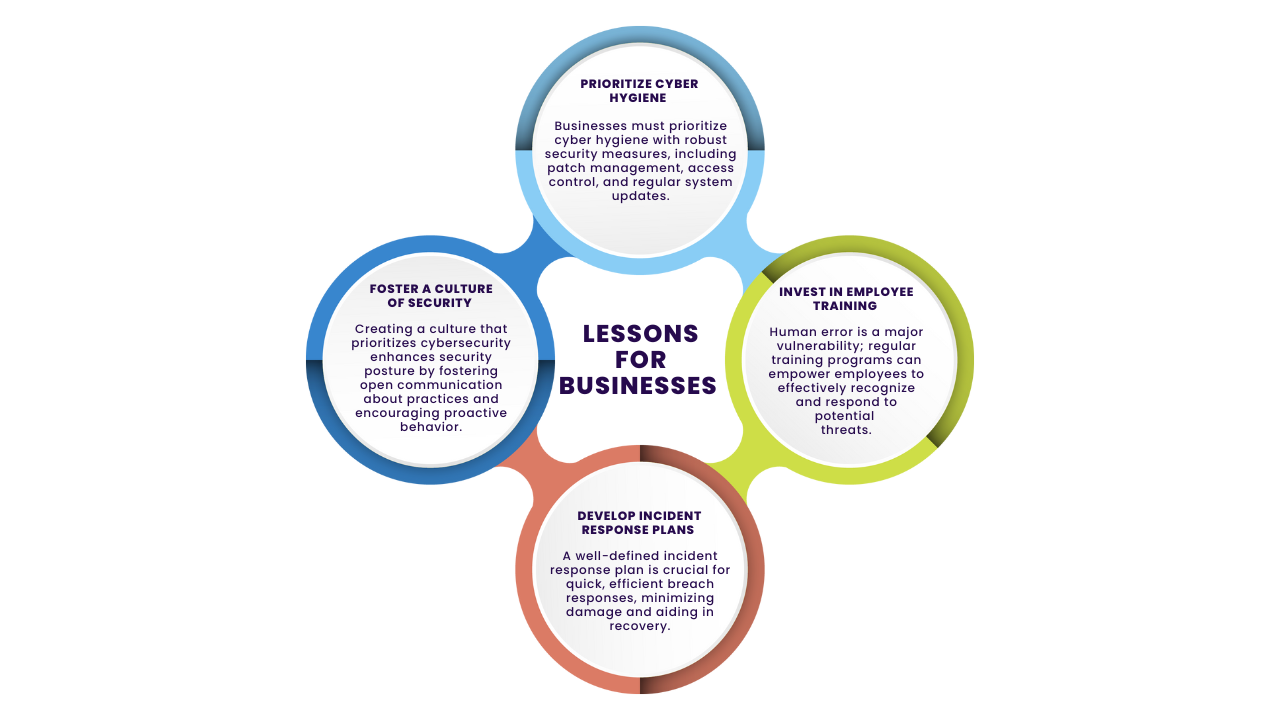
July 2024’s security incidents serve as stark reminders of the ever-present and evolving nature of cyber threats. The Disney breach, the Windows update issue, and the AT&T data breach each underscore different vulnerabilities and lessons for the business world. As business leaders, staying vigilant and proactive in implementing robust cybersecurity measures is imperative. Regular audits, continuous monitoring, and comprehensive employee training are essential components of a strong cybersecurity posture.
By learning from these incidents and investing in cutting-edge security solutions, businesses can better protect their data, maintain customer trust, and ensure operational continuity in the face of ever-evolving cyber threats. The stakes are high, but with the right strategies and mindset, we can navigate the complex landscape of cybersecurity with confidence and resilience.



