
Are you confident that your employees can spot a spoofed email from a legitimate one? In today’s rapidly evolving cyber landscape, cybercriminals are leveraging increasingly deceptive tactics like spoofing and phishing to breach business systems. While both are dangerous, they aren't the same. Understanding the differences between spoofing and phishing is key to ensuring your company remains secure.

While both involve deception, spoofing and phishing are distinct in their objectives and methods. Knowing how each works is essential for businesses looking to enhance their cybersecurity.
Spoofing is the act of disguising communication so that it appears to come from a trusted source. In email spoofing, attackers forge the sender's address to make the email look like it came from a legitimate entity such as a coworker, supplier, or government agency. This kind of deception can also occur in other forms, such as spoofing IP addresses or phone numbers.
Imagine receiving an email from “hr@company-secure.com” instead of your real HR department's “hr@company.com.” At a glance, this might go unnoticed, especially by busy employees handling multiple tasks.
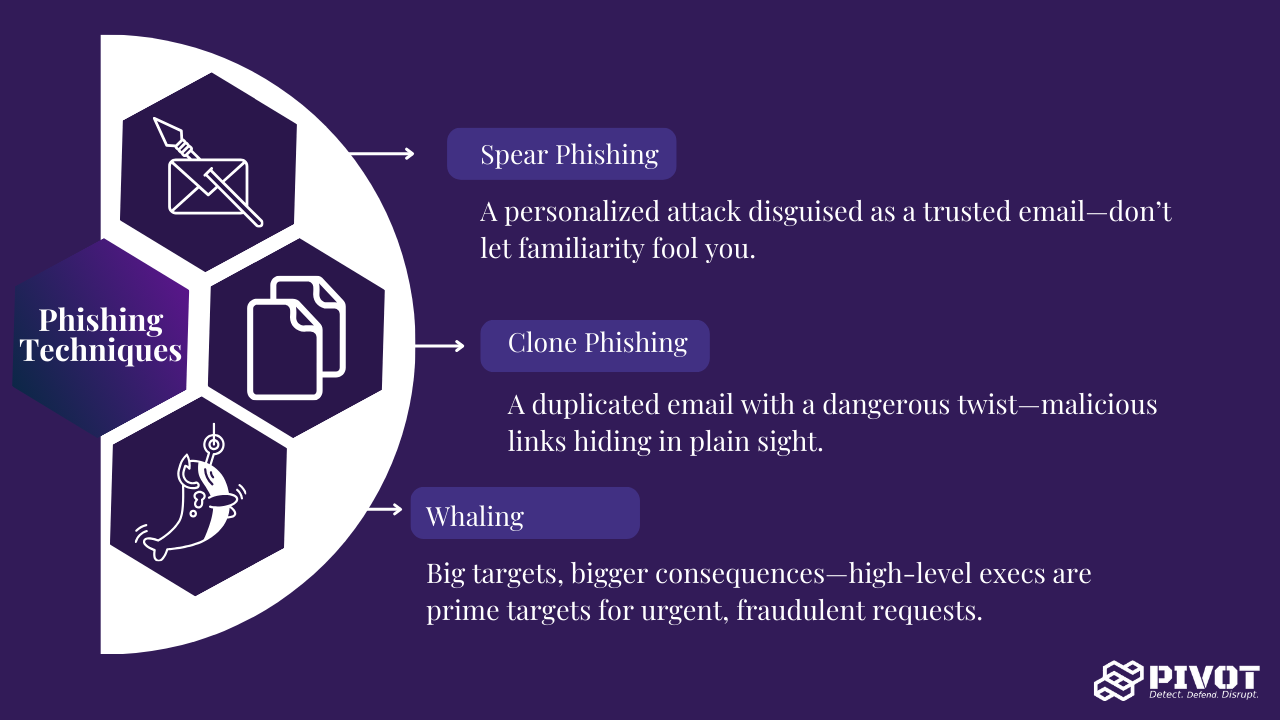
Phishing is a more targeted form of attack aimed at stealing sensitive information like login credentials, credit card details, or proprietary business data. Phishing often incorporates spoofing with emails crafted to look legitimate while containing malicious links or attachments that direct the recipient to a fraudulent site.
Consider you get an email that looks like it’s from your bank asking you to verify your account details via a link. Clicking the link leads you to a fake website designed to capture your login credentials.
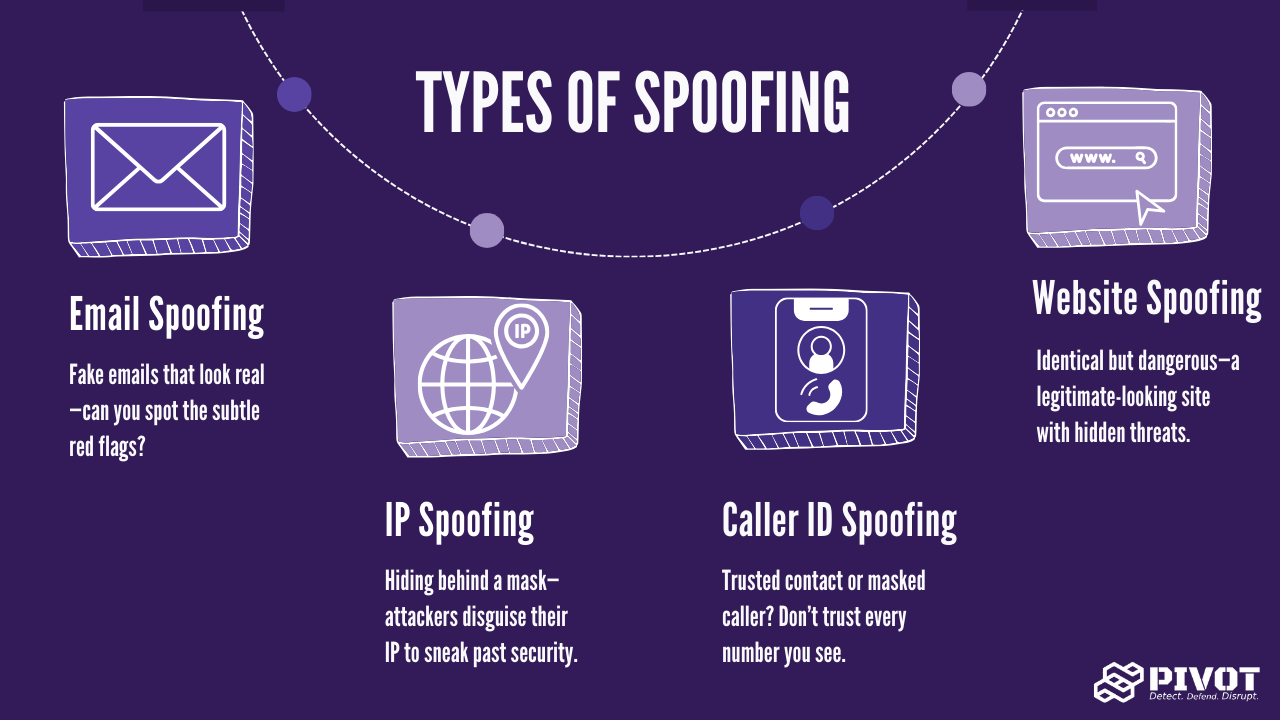
To better safeguard your business, it’s important to understand the various forms these attacks can take.
A phishing email might come from a spoofed CEO email address asking finance for a quick wire transfer. The subtle difference in the email address can easily go unnoticed in the rush of the workday.
In 2023, phishing accounted for 90% of successful data breaches. These attacks are growing more sophisticated and personalized, putting businesses at even greater risk.
For business owners, the consequences of spoofing and phishing can be severe, ranging from data theft to significant financial loss. Understanding how these tactics work is the first step to protecting your organization.
Both spoofing and phishing lead to unauthorized access to sensitive information. Attackers may trick employees into transferring funds, sharing passwords, or divulging confidential business data. With email spoofing, an attacker can impersonate key members of your team, leading to fraudulent activities or data breaches.
A spoofed email from what appears to be your CFO urgently requests a wire transfer to a new vendor. In the rush to meet deadlines, your accounting team processes the payment, only to realize it was a scam.
Once a hacker gains access to an employee’s login credentials, they can infiltrate your internal systems, steal sensitive data, or even deploy ransomware. A study by IBM found that the average cost of a phishing attack for businesses in 2023 was $4.65 million, making phishing one of the most expensive and prevalent cybersecurity threats.
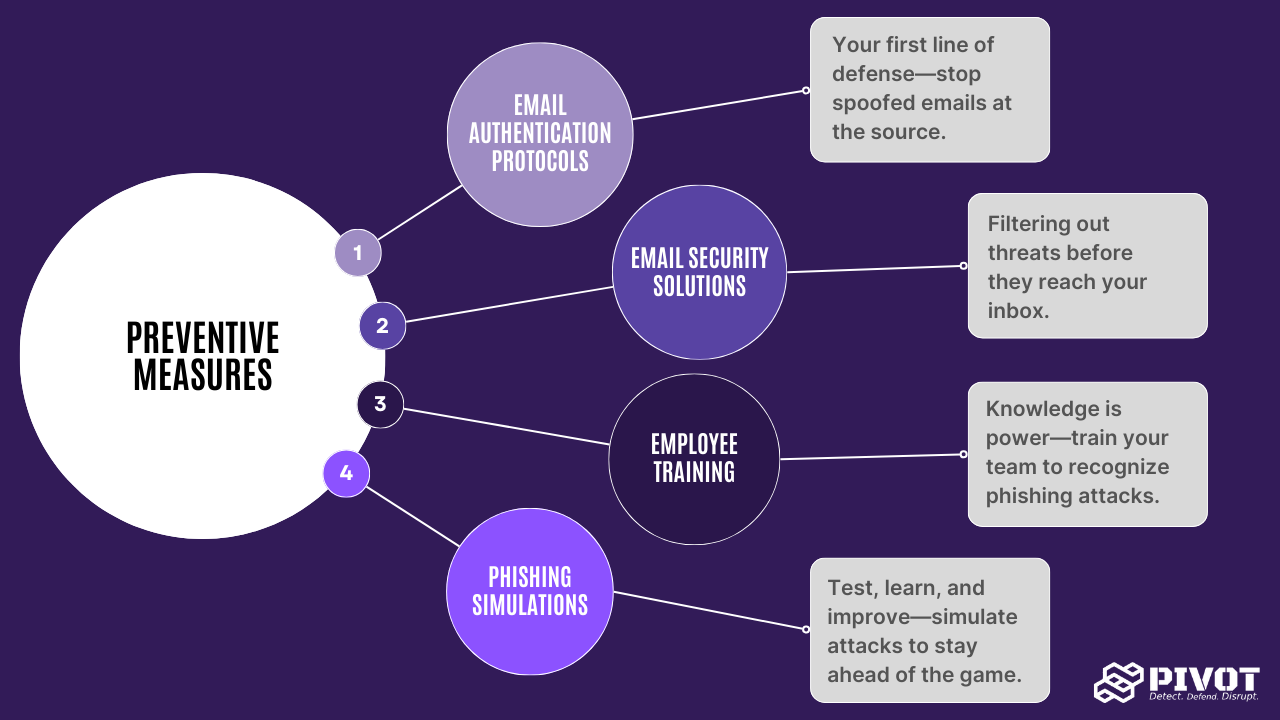
Preventing spoofing and phishing requires a multi-layered approach. Here are a few strategies business owners should adopt to protect their companies:
Email Authentication Protocols
Email authentication tools like DMARC and SPF can help detect and block spoofed emails before they reach your employees. These tools verify if the email sender is authorized to use the domain, greatly reducing the chance of a spoofed email landing in your inbox.
Email Security Solutions
Advanced email security solutions use machine learning and behavioral analysis to detect suspicious patterns, phishing attempts, and malicious attachments or links. These systems provide an extra layer of protection by filtering out harmful content and blocking potentially dangerous emails before they reach your employees' inboxes, significantly reducing the risk of phishing attacks.
Employee Training
Regular phishing awareness training is crucial in preventing successful attacks. Educate your employees about spotting phishing attempts and recognizing signs of email spoofing. Frequent, realistic training sessions keep your staff vigilant and prepared.
Phishing Simulations
Phishing simulations, such as those offered by Pivot Security’s Phish-e, allow you to test how well your employees can handle real-world phishing scenarios. By mimicking actual phishing techniques, you can identify vulnerabilities and improve security protocols.
At Pivot Security, we provide businesses with a powerful tool to combat phishing: Phish-e, our cutting-edge phishing simulator. With Phish-e, you can test your employees' resilience to phishing attempts and strengthen your cybersecurity defenses.
With Phish-e you’ll be able to:
Phishing and spoofing threats aren’t going anywhere. Protect your business before it’s too late. Visit Pivot Security to learn more about how Phish-e can help you safeguard your organization from phishing, spoofing, and other cyber threats.
Sources:



