
Have you ever wondered why despite all the security measures, a suspicious email still finds its way into your inbox? If you think it's just another piece of spam, think again. Phishing emails are more sophisticated, more targeted, and potentially far more dangerous than regular spam.
Before we dive into how phishing emails bypass spam filters, it’s essential to understand the distinction between phishing and spam as they’re often confused.
Spam refers to unsolicited bulk emails, usually promoting products or services. Think of those endless marketing emails from companies you’ve never heard of. While annoying, most spam is relatively harmless, aimed at advertising or nuisance-level fraud.
Phishing, on the other hand, is a targeted attempt to steal sensitive information such as usernames, passwords, and financial details. These emails are crafted to deceive, often masquerading as legitimate communication from trusted sources like banks, government agencies, or even your own organization. The stakes are much higher with phishing, as a single successful attack can lead to severe data breaches or financial losses.
Spam filters use two basic methods to identify if an email falls in the category of spam or not:
Only once the domain reputation is validated does the content analysis begin. Some advanced solutions utilize AI to identify spam emails from legitimate ones. AI works on pattern recognition and tone identification of the email. In any case, AI or not, these two checks are the major techniques spam filters rely on.
Attackers are aware of these two requirements. Even phishing simulation tools use these basic principles to make employees aware of the threat phishing poses.
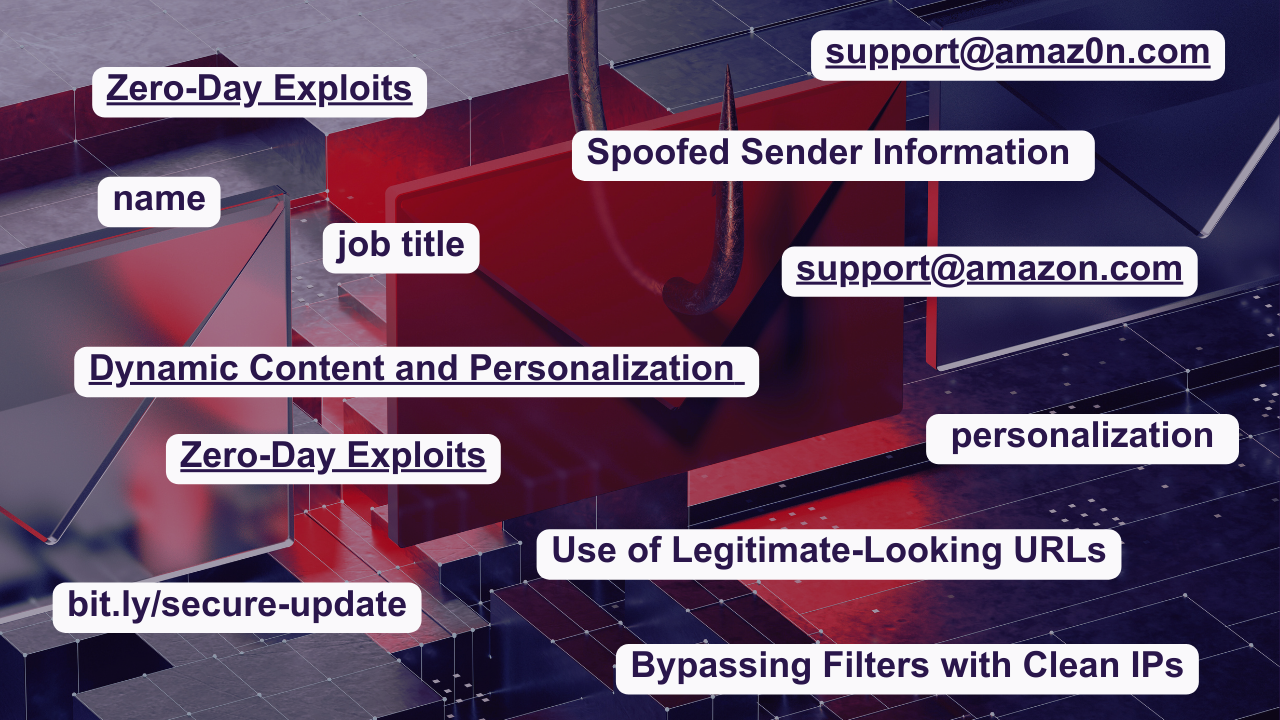
Spoofed Sender Information
Phishers often mimic legitimate senders by creating email addresses that closely resemble those from trusted entities. For example, an email might appear to come from "support@amaz0n.com" instead of "support@amazon.com". This tiny change can easily go unnoticed by the recipient and even some spam filters. This tactic is a common form of email spoofing, making it difficult for both users and systems to identify the deception.
Zero-Day Exploits
Phishing attacks frequently exploit new vulnerabilities that are unknown to security vendors and spam filters. Known as zero-day exploits, these attacks use loopholes in the system that haven’t been patched, making them extremely difficult to detect and prevent. Such vulnerabilities contribute to the effectiveness of spam filter evasion techniques used by cybercriminals.
Dynamic Content and Personalization
Unlike generic spam, phishing emails are often tailored with personal information to appear more credible. They might include your name, job title, or even recent activity to make the email look legitimate. This level of customization makes it harder for spam filters, which rely on detecting repetitive patterns to flag these emails. Phishing email characteristics such as personalization and dynamic content make them particularly dangerous.
Use of Legitimate-Looking URLs
Phishers cleverly disguise malicious links using URL shorteners or domain lookalikes. A link might appear as a legitimate site (e.g., “bit.ly/secure-update” instead of “secure-update.com”), leading you to a fraudulent login page. This tactic fools both the recipient and many spam filters. Identifying phishing attempts requires vigilance, as these URLs can be easily mistaken for legitimate ones.
Bypassing Filters with Clean IPs
Spam filters often rely on blacklists of known malicious IP addresses. Phishers use clean IP addresses or constantly switch to new ones to avoid detection. They also employ techniques like “snowshoe spamming” — sending low volumes of emails from multiple IPs to fly under the radar.
For business owners, the implications of phishing attacks are far-reaching. One successful phishing email can compromise sensitive business data, lead to financial loss, or even damage your company’s reputation. Even a single employee clicking on a phishing link can result in a costly data breach.
In 2023 alone, the average cost of a data breach resulting from phishing attacks was $4.65 million, according to a recent report by IBM Security.
Invest in Advanced Threat Detection
Basic spam filters won’t cut it. Invest in advanced threat detection solutions that utilize machine learning and behavior analysis to identify unusual email patterns and suspicious content. This will help you better identify and prevent scam emails from reaching your employees.
Regular Employee Training
Employees are your first line of defense. Conduct regular training sessions and phishing simulations to educate your staff on how to spot phishing attempts and what to do when they encounter them. Understanding phishing email characteristics is crucial for every team member.
Phishing Simulations
Testing your employees with simulated phishing attacks is a proactive way to assess their vigilance and improve your security posture. By mimicking real-world phishing techniques, you can identify vulnerable areas and strengthen your defenses.
At P.I.V.O.T Securities, we specialize in phishing simulations that replicate real-world attack scenarios, helping you stay ahead of cybercriminals. Our platform offers:
Don’t Wait for a Phishing Attack to Happen
Protect your organization before it’s too late. Check out our phishing simulator Phish-E to learn more about how it can help you build a resilient defense against phishing attacks. Secure your business today!




